Stored XSS leads to account takeover in Flarum
Trung Nguyen
| CyStack Advisory ID | CSA-2022-01 |
|---|---|
| CVE IDs | CVE-2022-41938 |
| Severity | Critical |
| CVSS v3 Base | 9.0 |
Synopsis
CyStack’s researchers recently discovered a Stored XSS vulnerability in the Flarum platform version 1.5.0 to 1.6.1 which can lead to an account takeover attack. Flarum is a widely used simple and open-source forum platform. At the time of this post, we estimate that there are about 1200 active Flarum websites.
Exploiting this vulnerability is very simple as the attacker just needs to create a post that included the payload on the target forum and wait for forum users to access the post. The attacker can then obtain cookies from the victims and take over their accounts on the forum.
CyStack reported this issue to the Flarum team via their bug bounty program and got confirmation from the team. A patch and announcement were released quickly after that at https://discuss.flarum.org/d/31999-critical-security-update-to-flarum-core-v162
Details
The title is a required field when a user creates a discussion in the forum. The problem here is that developers did not sanitize this variable before rendering to the HTML, which resulted in the attacker being able to generate malicious payloads and attach them to the title field when creating the post. Once the victim opens this post, a payload will be executed that can steal user cookies.
According to the Flarum team
Flarum’s page title system allowed for discussion title inputs to be converted into HTML DOM nodes when rendered (visiting a discussion page). This change was made in v1.5.0 and was not noticed.
This allowed for any user to type malicious HTML markup within discussion title user input, either through a new discussion o renaming an existing one, and have this execute on client browsers. Entering faux-malicious HTML markup, such as
https://discuss.flarum.org/d/31999-critical-security-update-to-flarum-core-v162<img src=x onerror=alert(document.domain)>resulted in an alert box appearing on the forum. This attack could also be modified to perform AJAX requests on behalf of a user, possibly deleting discussions, modifying their settings or profile, or even modifying settings on the Admin panel if the attack was targeted towards a privileged user.
PoC
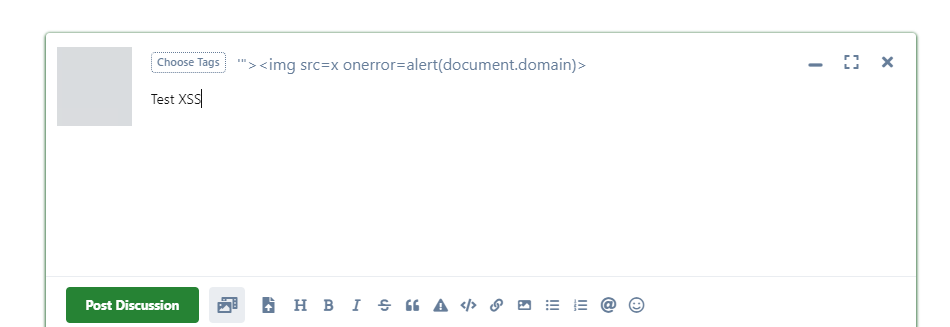
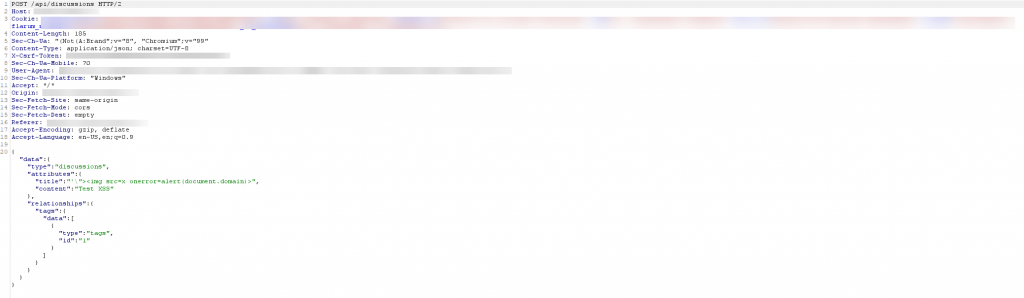
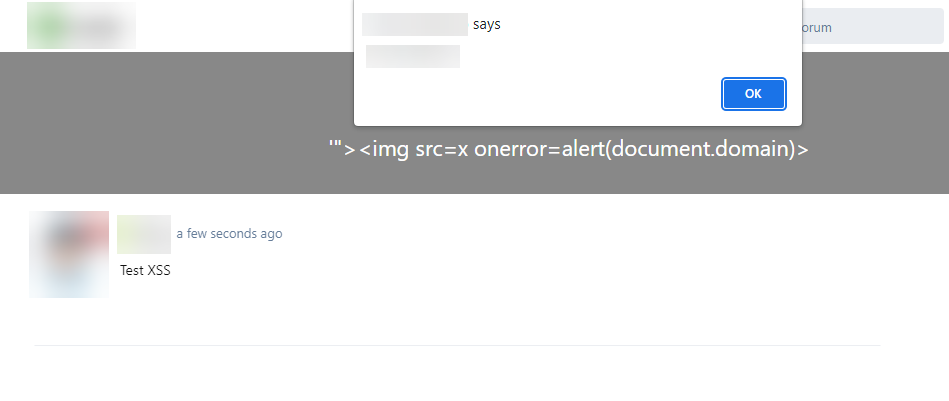
Remediation
Flarum users should update their platform to the latest version (>=1.6.2) according to the below instruction
# Update to latest version
composer update --prefer-dist --no-dev -a -W
# Verify that you're on v1.6.2
composer show flarum/core
# Clear cache
php flarum cache:clear

