
Penetration testing (pentest) plays a critical role in software development. So, what is pentest? How does it contribute to corporate cyber security?
>> Checklist 11 Things To Know: Pentest Testing Service Or Recruiting A Pen-tester
What is Pentest?
Penetration testing
A pentest is an attempt to test the IT infrastructure security by a simulated cyber attack. A pentest is trying to attack your computer to check for exploitable vulnerabilities.
The main goal of a pentest is to explore vulnerabilities and fix them. A person who implements a pentest is called a pentester.
>> Crowdsourced Penetration Testing Service
Pentest can be used for various types of infrastructure. For example computer systems, web apps, mobile apps, cyberinfrastructure, IoT, applications and cloud infrastructure, SaaS, API, source code, or any subject connected to the internet, etc. All these components are pentest targets.
Pentester needs the approval of the admin system or admin application to test the system. If not, this attack will be illegal. In fact, the only difference between a pentest and a malicious hack is the permission of the target owner. Thus, pentest has the same meaning as ethical hacking, and a pentester is also called a white hat hacker.
To understand pentest, you need to understand the concepts: vulnerabilities, exploits, and payloads.
- Vulnerabilities are security flaws that weaken the security system. The vulnerability may be a weak password, SQL flaw, or buffer overflow.
- Exploits are programs or pieces of code that harm the computer system. Cybercriminals can cause privilege escalation attacks, data breaches, DDoS attacks, etc.
- Payloads are parts of the system that contain security flaws and might be targets of attacks.
Types of pentest
- White box testing: Researchers are provided with information about pentest targets before testing. The information includes IP addresses, network infrastructure diagrams, protocols, or source codes.
- Gray box testing: Pentesters can not access the targets. They only receive partial information such as URL, IP address, etc.
- Black box testing: It is also known as “blind testing”. A pentester acts as a hacker attempting to attack the target without any information. The pentester has to collect information and test. This type of testing requires a large amount of time and effort, so the cost is quite expensive.
Other types of testing: double-blind testing, external testing, internal testing, and targeted testing. But, these types are only used for specific demands of some enterprises.
History of Penetration Testing
In the mid-1960s, there was a sharp increase in the ability to exchange data via the computer network. And experts warn about threats of attacks on government and business networks. In 1967, researchers suggested the use of “penetration” in a security conference. Researchers consider penetration as a threat to exchanging data through the computer network.

In 1967, RAND Group and the Defense Advanced Research Projects Agency (DARPA) in the United States released the Willis Report (named after the project lead). This report laid a foundation for modern security measures. The U.S government cooperated with enterprises to establish working groups. Their purpose is to explore security vulnerabilities to prevent illegal penetration and exploration.
One of the first pentest teams in the world is Tiger Teams (named after the U.S Special Forces). The team was founded in the late 1960s. It aimed to test the ability to defend against attacks on the computer network. The result was surprising:
“Most of the system was attacked easily.”
The pentest campaign of RAND corporation and the U.S government proved that:
- First, systems can be exploited
- Second, pentest is an efficient way to explore vulnerabilities in the network system
Lately, Deborah Russell and G.T.Gangemi Sr. stated that:
“The 1960s marked the true beginning of the age of computer security.”
Deborah Russell & G.T.Gangemi Sr.
Why do we need Pentest?
Along with technology development, pentest has become an indispensable part of information security systems.
Penetration Testing is an effective security solution to prevent web, mobile apps, networks, IoT, etc. from malicious attacks. Through simulated attacks, pentesters find security flaws. Then enterprises patch these vulnerabilities before malicious hackers can exploit them.
According to Market Watch – a market research firm, the pentest market will reach $2420 in 2025 with a growth rate of 14.9%. The demand for pentesting is increasing. There are four reasons for the growth in demand for pentesting.
Four reasons why pentesting is essential for a modern business
Increase in the web app and mobile app
Nowadays enterprises need to use websites or mobile apps to approach – connect – communicate – support customers. Digitalization is not only a compulsory need but also an advantage for an enterprise. Users’ behavior is changing, they prefer to do everything “online”. Thus, enterprises can reduce the costs of inventory, and renting. Yet, they have to face cyber security risks such as hacked websites, hacked mobile apps, data breaches, malware, operational disruption, etc.

Digital transformation
More and more enterprises have implemented digital transformation. Technology helps enterprises to reduce human resources, and operation costs. But digitalization increases the attack surface for hackers. Some examples of attack surfaces are ERP, CRM, IoT devices, etc. If these digital properties are not protected safely, they can be easy victims of cybercriminals.
SaaS
Software as a Service (SaaS) is software licensing in which software is licensed on a subscription basis. SaaS is increasingly used by businesses. It is very convenient for end-user when subscribing to a SaaS product. But, providers have to face more security threats. SaaS, IaaS, PaaS, FaaS requires a constant internet connection. Thus, the possibility of DDoS increases and users’ experience will be affected.
An efficient prevention
Finally, enterprises can gain more benefits from simulated-attack security than traditional security. Pentesters attack with a mindset as malicious hackers in reality: “human” and creative.
Advantages of Pentest
If enterprises launch pentest properly, they will gain important security targets:
- Improve security for the IT system. Including web applications, mobile applications, networks, IoT, API, cloud systems, SaaS, and hardware. Enterprises can cut the risks of illegal penetration and damage
- Leaders have a look at the big picture of product security
- Estimate the loss of an actual attack
- Protect data system, sensitive information of enterprises and users
- Ensure the stable performance of the infrastructure. And reduce the possibility of DDoS attacks
- Explore critical vulnerabilities that automatic tools can not find
- Ensure specific security standards (PCI DSS, HIPAA, ISO 27001, etc.)
- Strengthen the faith of customers, partners, and investors
The proper time to launch Pentest
Enterprises should run pentest annually or quarterly to ensure IT infrastructure security. Besides, pentest will be necessary for some specific occasions:
- Release IT infrastructure or new application
- Update or adjust applications and infrastructure considerably
- Move to the new office and reset the system
- Release new security patches; or
- Adjust privacy policy for the end-users
>> Penetration Testing Service
What types of enterprises need pentest?
Pentest is not for every organization. Enterprises have to consider the following factors before running pentest programs:
- Online frequency: if a company is online at a high frequency, it will have more attack vectors. Such companies are more attractive to cybercriminals
- Cloud infrastructure: if enterprises use the cloud infrastructure of a third party. Then they are not allowed to run pentest on the cloud infrastructure. But the providers must launch pentest to ensure security for their customers
- Budget: cost of a pentest program is not cheap. Thus companies having a limited budget for security will have difficulty in pentesting
Weakness of Pentest
Although pentest can defend against cyber-attacks, it still has some drawbacks:
- High cost: enterprises often pay pentesters by hours or days, and the cost is not cheap. In fact, many enterprises need penetration tests. But high cost prevents them from taking action
- Lack of diversity: a pentest team often consists of 3-5 members. They follow a fixed and repeated process. In reality, there is not any certain process for malicious hackers. Moreover, the number of them is so large that there will be many different methods to attack your system
- Ability to integrate into SDLC: a report is usually a long list of vulnerabilities. There is no integration into the software development process. Thus, enterprises have to spend more on operation costs. Besides, they also have to slow down the pace of fixing and developing applications
>> Drawbacks of Traditional Pentest
Crowdsourced penetration testing can overcome these shortcomings. Crowdsourced pentest helps enterprises reach hundreds of pentesters. Including security experts, or white hat hackers. Moreover, the bug bounty model allows businesses to optimize their investment in security.

Learn about Crowdsourced Pentest and how big firms like Google, Facebook, and Uber use it.
Crowdsourced Penetration Testing 101
Penetration testing tools
Pentesters often use tools to explore security flaws. These tools scan source codes to find malicious source codes. Besides, these tools can detect data encryption and hard-code values (username or password) to determine vulnerabilities in the system.
A good pentest tool must:
- Be easy to launch, set up, and use
- Scan the system easily
- Classify vulnerabilities based on severity and urgency
- Verify vulnerabilities automatically
- Recheck the previous exploits
- Export vulnerability report and detailed logs
There are many free pentest tools available like Metasploit Project, Nmap, Wireshark, and John the Ripper. Pentesters use the same tools as black hat hackers. So pentester can understand the way that malicious hackers attack the pentest targets.
“Professional pentesters use tools to save effort as well as optimize their efficiency.”
Pentest procedure
There are different methods and approaches to penetration testing. Yet, they have four common basic steps:
- Reconnaissance
- Enumerate
- Exploit
- Documentation
Reconnaissance
In this step, pentesters collect all information about the pentest targets. This process makes a huge impact on the result of pentesting. If pentesters collect the information in the right way, they can shorten the testing duration many times. Information collected includes the website address, server type, server location, link, encryption standard, contact, email, and phone number. They use a wide range of tools to collect such information such as Google Search, Nmap, or Wireshark. Sometimes, pentesters also analyze the source code of the website to gather information.
>> Reconnaissance Overview by Hoàng Nam Dương
Enumerate
The next step is to determine the entry point of the applications. Pentesters use their experience as well as tools to find all possible points to access the applications. Popular tools used are Nmap and Wireshark.
Exploit
Pentesters exploit vulnerabilities to gain access to the web or mobile applications.
Documentation
When pentesters successfully penetrate the system, they need to send reports to the system administrator to verify and evaluate the vulnerabilities. In this step, pentesters have to create a Proof of Concept (PoC).
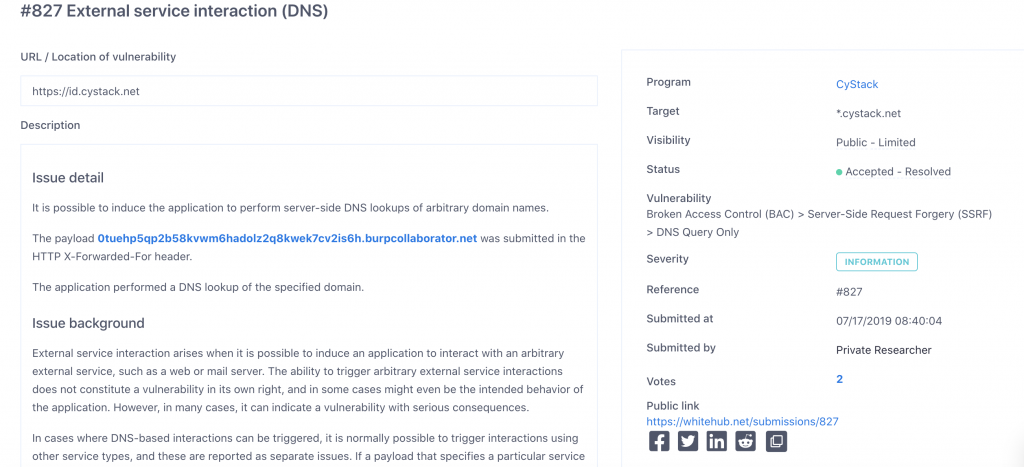
PoC expresses that a certain idea or method works. It shows that pentesters have been able to make use of a security flaw. A piece of code simulates the exploitation of pentesters, which is called PoC code. If the PoC code is spread widely before patching, a zero-day exploit might happen.
A pentest program is closed by mutual consent to the final report. They need to agree on the number of vulnerabilities and their impact on the systems.
Many pentesters can explore dangerous vulnerabilities. But they can not prove the impact of those vulnerabilities on the organizations. And enterprises do not highly appreciate such flaws. Thus the influence of vulnerabilities on the business is very important. Pentesters must understand the field of the organizations to discuss the impact.
Pentest web app, mobile app service
CyStack is one of the most reputable security companies. We provide professional Pentest services for many small and medium enterprises.
Taking advantage of the WhiteHub platform, CyStack Pentest has outstanding advantages:
- 7x more effective than traditional pen-test projects
- Paid by each vulnerability
- Real-time report. PoC right away when a vulnerability is found
Our customers: Sendo, Giaohangtietkiem, Tomochain, VNtrip, VNDC, Getfly CRM, VinID, and many other enterprises.
 8 minutes read
8 minutes read
