Subdomain takeover – Chapter two: Azure Services
Trung Nguyen

As I described in the chapter one, we can control the content of a sub-domain d by controlling the content of domain d1 that d points to through its CNAME record.
Azure, a popular cloud service offer many services that can create such a d1. In this article, I will go details about services of Azure that can be vulnerable and how I exploited in the wild, including: Traffic Manager Profile, Web App, Virtual Machine
Traffic Manager Profile
Traffic Manager profiles use traffic-routing methods to control the distribution of traffic to your cloud services or website endpoints.
My targets: Microsoft, Deloitte, HP
Normally, we can detect that a domain is using Traffic Manager if its CNAME record is xxx.trafficmanager.net like the following case.
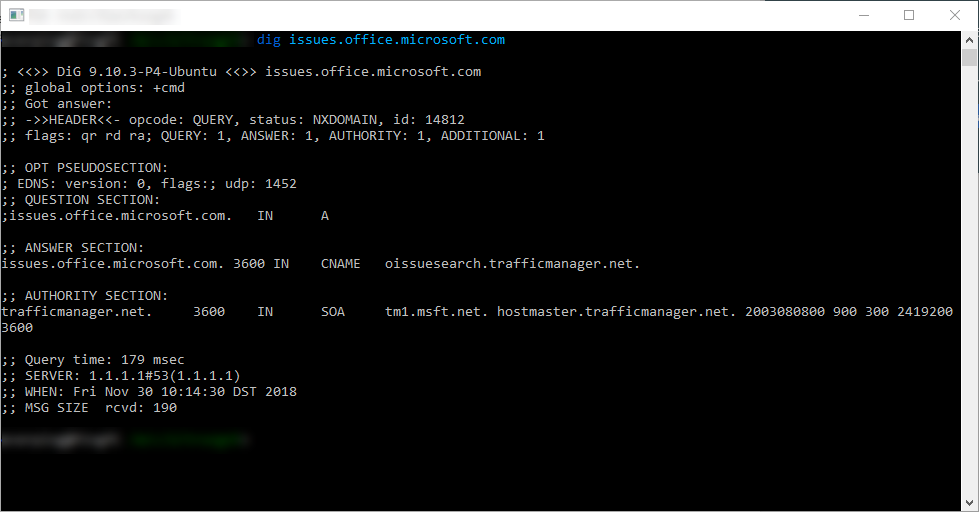
The next step is checking whether the CNAME domain is available to register or not by using Azure API or using Azure portal.
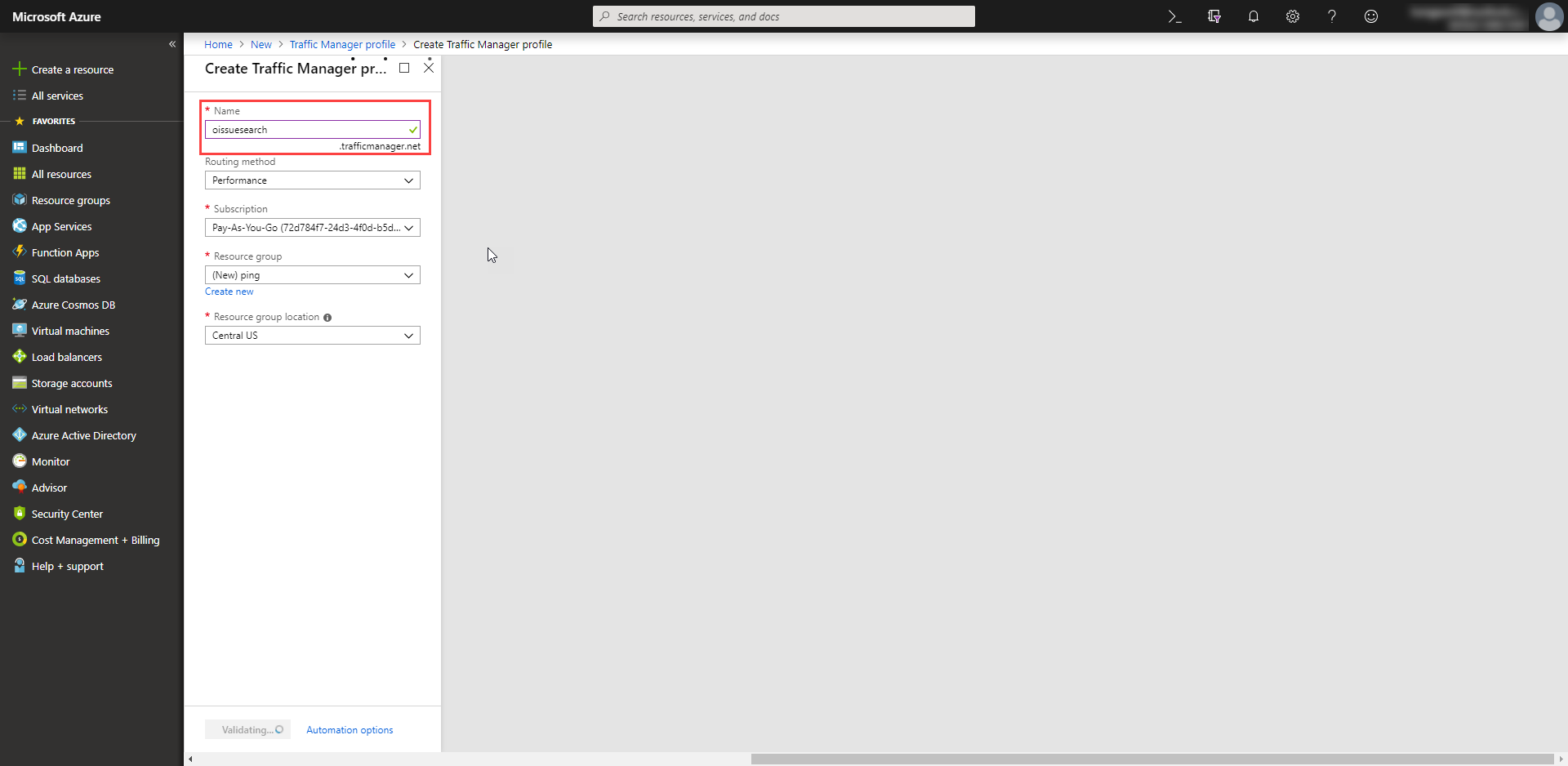
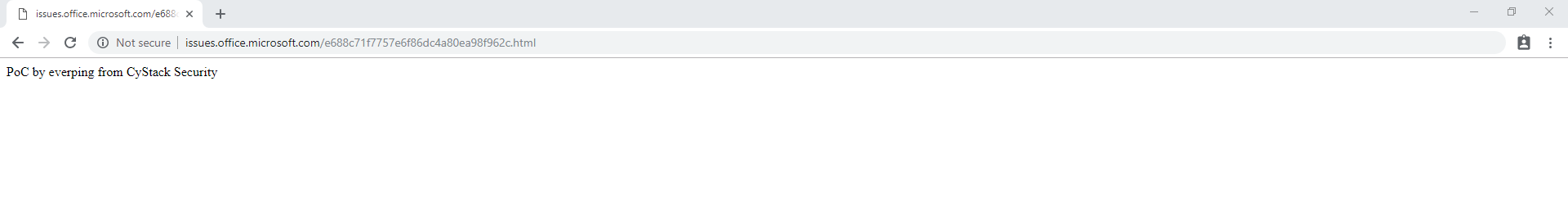
If it is available, just create then in endpoint setting, select type External endpoint and enter your controlled IP address as the target. The final step is to create a PoC page in your server to make the PoC works.
Web App Service
Azure App Service enables you to build and host web apps, mobile back ends, and RESTful APIs in the programming language of your choice without managing infrastructure
My targets: Deloitte, US gov
In this case, the original domain points to xxx.azurewebsites.net
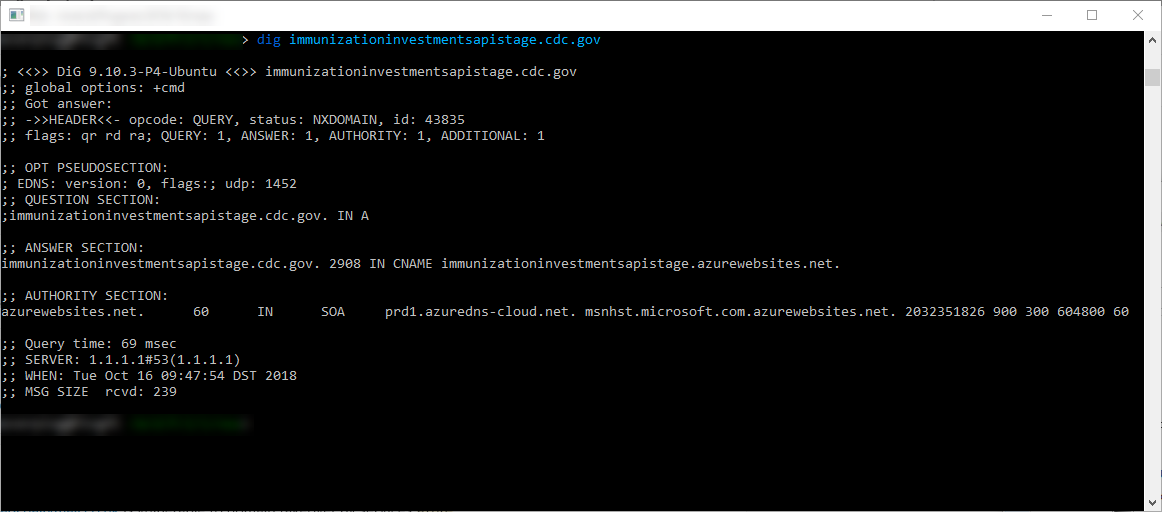
Similar to the Traffic Manager Profile, we have to check check the destination domain’s availability and if it’s available, create your own app. Then push whatever you want to it to prove that you can control the domain.
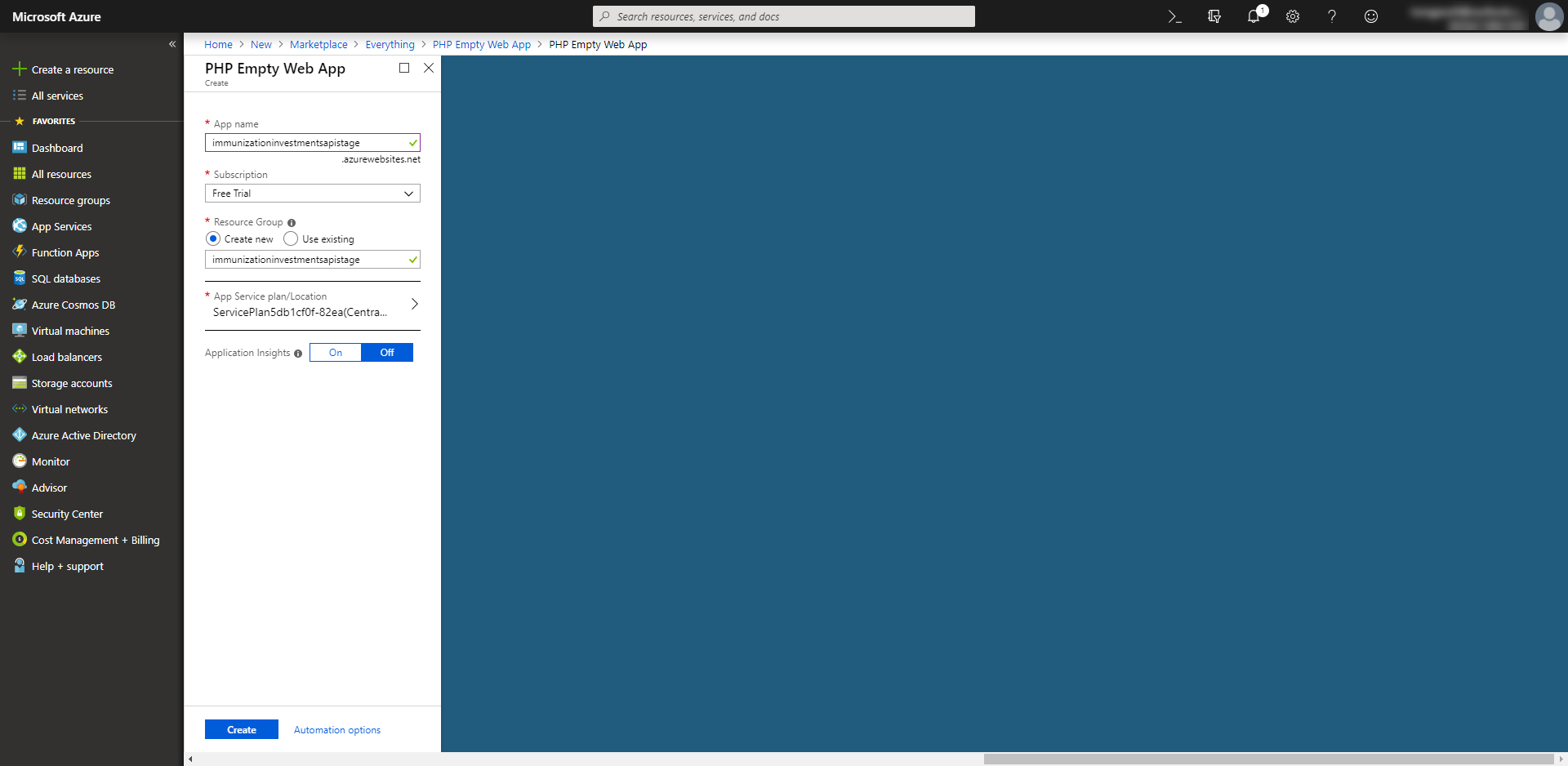
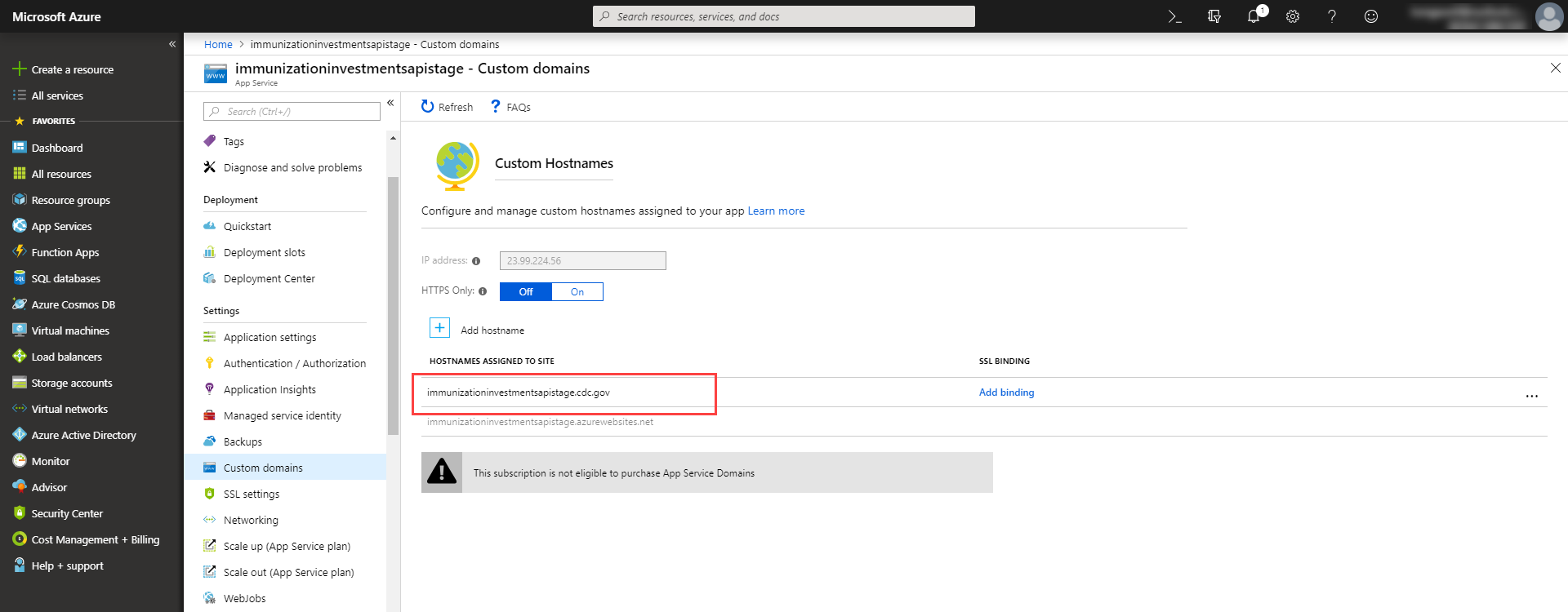
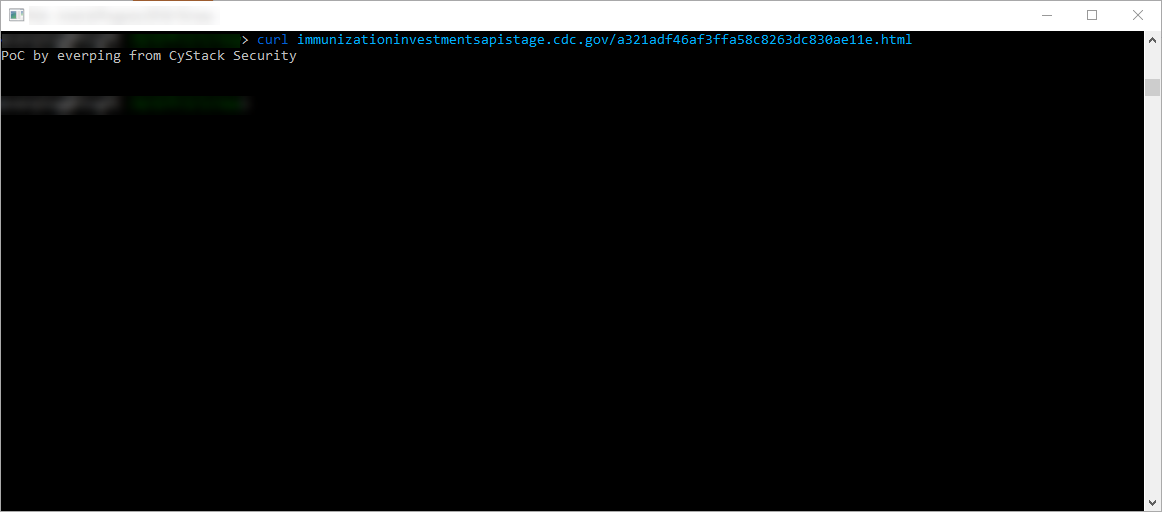
Note: I have reported that bug to the US Cert and they fixed afterwards.
Virtual Machine
Azure Linux Virtual Machines provides on-demand, high-scale, secure, virtualized infrastructure using Red Hat, Ubuntu, or the Linux distribution of your choice
My targets: BBC
Compare to those cases, the destination domain in this case includes the region name, its form is xxx.region_name.cloudapp.azure.com
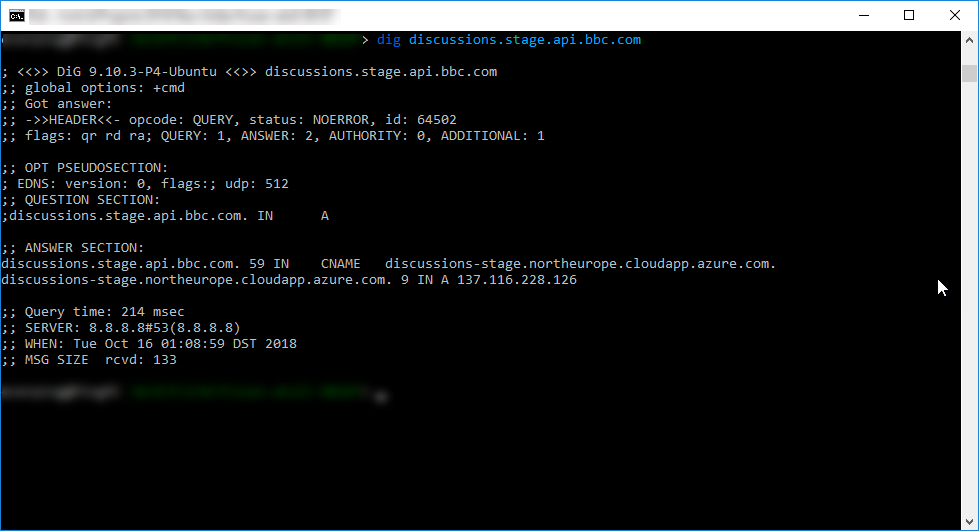
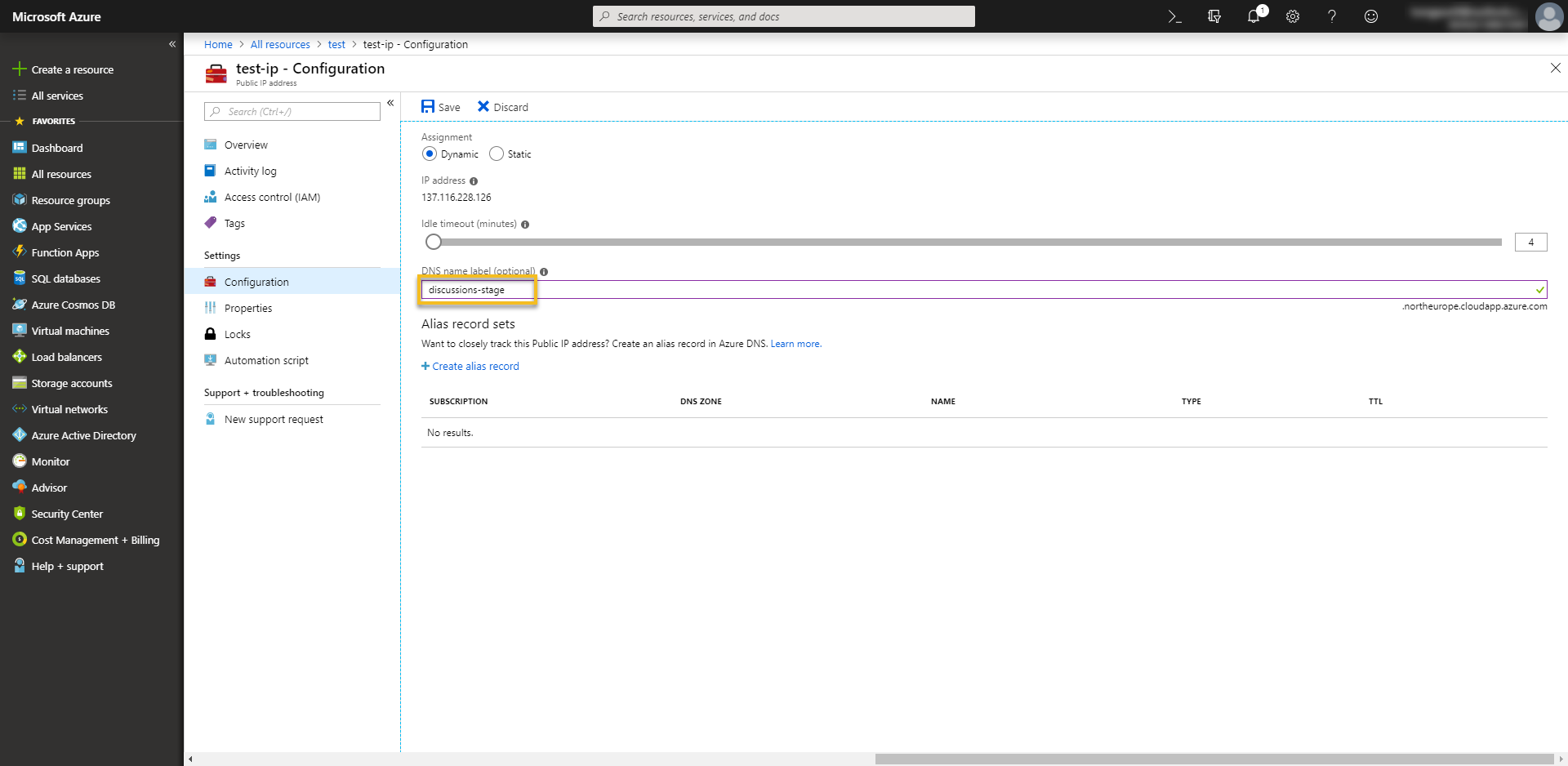
Steps to exploit
- Create a Virtual Machine, Ubuntu server for example. You must select the correct region with the region in that CNAME. In this case, it is
North Europe - In Overview setting, change DNS name to
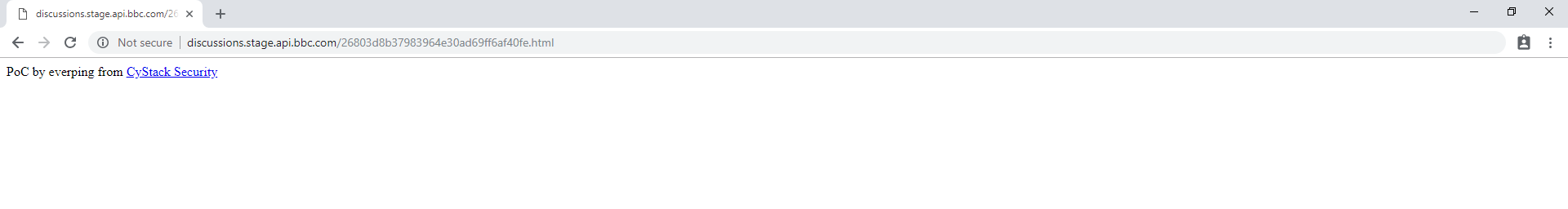
discussions-stage.northeurope.cloudapp.azure.com - Install a webserver (Apache, Nginx) in the VM just created and create a virtual host for it to serve requests to
discussions.stage.api.bbc.com
Fun facts
- Roughly 40 domains of Microsoft affected by this issue. Their security team responded quite slowly and did not reward for the finding since it is out of scope. However, they gave me a sincere thanks and acknowledged me in MS Hall of Fame (2 times for 2 reports)
- BBC gave me a T-shirt and acknowledged me their Hall of Fame
- About 140 domains of Deloitte, one of the world’s largest auditing companies, are vulnerable. Reporting bugs to them is probably one of the worst experiences in my career. When I found issues in their domains, I tried to find their security contact but got nothing; I also sent emails to the addresses I saw on their official websites but got no responses after 1 week. Finally, I used Linkedin and texted to some people that I think they work there, one of them replied me that she forwarded my message to the security team. Sadly, she just quit her job there for a short time. The security team then contacted me and asked me for details. What happened after that was that they said they received the information and ended the conversation. I’m also not sure if those problems have been fixed. Honestly, I have no intention of reporting the vulnerability to this company anymore.


