Subdomain takeover – Chapter one: Methodology
Trung Nguyen
Subdomain takeover is a high severity vulnerability that can be exploited to take control of a domain and pointing it to an address managed by attackers. Attacks on this vulnerability are often used for the purpose of creating phishing sites, spreading malwares. However, subdomain takeover is not a new vulnerability, it may be published from the year of 2014.
On the last weekend of October, I spent some time coding exploits to find major websites that could be affected by the vulnerability. The results were very unexpected, I found more than 200 domains affected by the vulnerability just in 2 days. These domains belongs to big technology, finance companies and major newspapers. I suppose that I should share my discoveries with subdomain takeover, so this series will show my perspective, how do I find out vulnerable websites and how to exploit them, on a case by case basis.
Domains and IP addresses
To begin with, let’s talk about a typical example. You own a domain example.com and a server with the IP address 1.2.3.4. Now you would like to point your domain to this IP address?
Normally, your DNS providers offer several ways to do this, including:
- Using A or AAAA records
- Using CNAME records
- Using extra records like ALIAS or URL records
We will look into the details in each of these ways
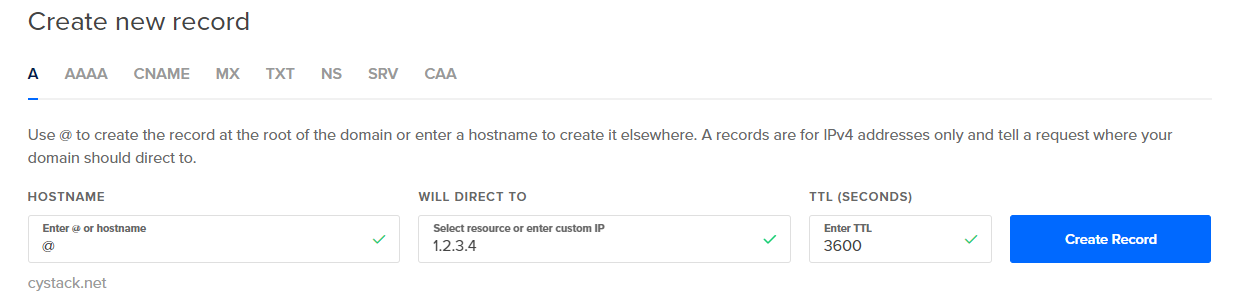
Using A or AAAA records
This is the most common way, almost everyone who works with domain names has ever used this method. We will have to enter a host and a value as the domain name and the IP respectively.
Notes:
@used to point a root domain (example.com) to the IP addressxxxused to point a sub-domain (xxx.example.com) to the IP address- A records are for IPv4, while AAAA records are for IPv6
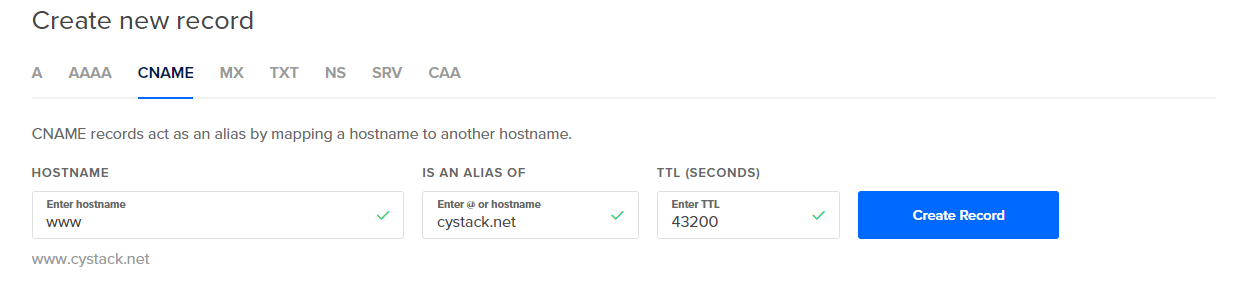
Using CNAME records
A/AAAA records is a direct solution for the domain name resolution. However, in some cases this method will cause annoyance, for example:
- You own 100 subdomains (
x1.example.com,x2.example.com…x100.example.com) and all of them are pointed to the IP1.2.3.4. One day, you changed the host and the IP is changed to5.6.7.8. Would you update the A record for 100 sub-domains? - You are using a 3rd party service to create a landing page for your advertising campaign. This partner created a site with domain
yourcompany.ads.com. However, you wouldn’t like to use this domain, simply because it is unfamiliar to your customers. How to point your own domainlanding.example.comtoyourcompany.ads.com?
You can use CNAME records for these cases. CNAME is the most well known way to “symlink” one DNS record to another. It works by answering queries asking for the Source with a simple referral (by domain name) to the Target, which may be anywhere else on the internet.
For example 1, we will need to point subdomain x100.example.com to the destination IP by using the A record, then point 99 other sub-domains to x100.example.com by using the CNAME record. Later, if the destination IP is changed, we will just need to update the A record of x100.example.com.
For example 2, we will need to point the CNAME of landing.example.com to yourcompany.ads.com.
The biggest problem with CNAME is that it cannot be used for a root domain, but only sub-domains.
Using ALIAS and URL Redirect Records
These are records not in the DNS RFC, so they are only supported by certain DNS providers. ALIAS is a pseudo-record that works like a CNAME but can be used for both the root domain and sub-domains. The URL Redirect record is used to redirect a domain to another URL/domain name.
Subdomain takeover attack
The goal of this attack is to point a victim’s domain to an attacker’s address. This is closely related to the domain resolutions I have described above. In the case of using A/AAAA records for the resolution, it’s not worth mentioning but the remaining cases have weaknesses.
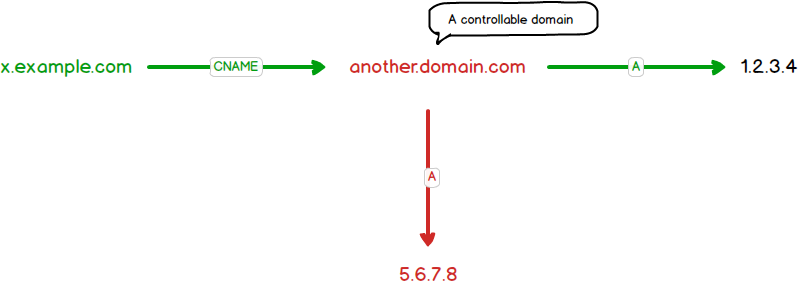
Let’s look at a scenario as follows:
- You own
x.example.com x.example.compoints toanother.domain.comby using a CNAME record
In order to control the content of http://x.example.com, we have to control the content of http://another.domain.com. This is possibile, if:
another.domain.comis an expired domain -> Buy this domaindomain.combelongs to an Internet service and it allows to create a sub-domain likeanother.domain.comif that name is available. You can find out many serives having that feature such as Github, Heroku, Amazon S3, Shopify, etc.
I did not think this attack was effective until I proceeded to find the subdomains of many big firms and checked the feasibility of the attack. As I said at the beginning, the results are verysurprising. One of them are microsoft.com, but subdomain takeover vulnerability is considered as out-of-scope of their bug bounty programs so I was only acknowledged in their Hall of Fame.
The method I used was:
- Find all subdomains from a domain by using SubStack
- Check the exploitable signature of sub-domains found. I have used signs published here as well as my own techniques.
In the next article, I will present more specific cases that I have successfully exploited.


