
Our topic today is DeFi security.
When you land on this page, you might have already heard of or even been using Decentralized finance (DeFi) to keep your money.
However, you may be concerned to know that this technology is also appealing to cyber criminals attempting to steal your assets. It was reported that 97% of cryptocurrency stolen in 2022’s first quarter was from DeFi protocols.
Worry less; in this article, we will provide best practices to protect your DeFi wallets! Scroll down now.
What Is DeFi?

Traditionally, centralized finance is the mainstream where third parties such as banks or corporations will keep and transfer money. You have to pay fees to use their services.
Meanwhile, decentralized Finance (DeFi) applies Blockchain technology to cut out the involvement of intermediaries and create a peer-to-peer financial system, so-called open and transparent finance.
Users worldwide can join DeFi protocols, following smart contracts rather than complicated legal obligations or paying high transaction fees. As a plus, they can control their money and review transactions transparently.
DeFi Security: Room for Improvement!
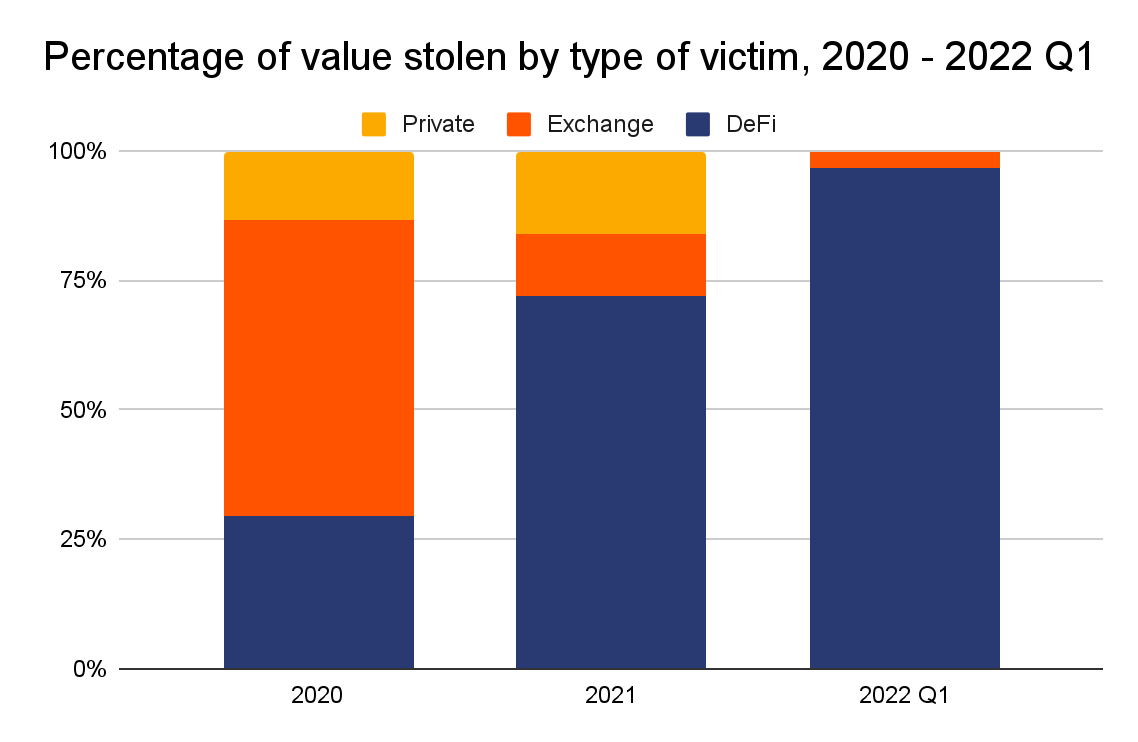
The 2022 Crypto Crime Report of Chainalysis has revealed an alarming fact: Only in the first quarter of 2022 did cyberpunks pocket 1.3 billion dollars from cryptocurrency transactions. Most victims were from DeFi protocols. This means DeFi has both high benefits and plenty of risks.
Here we give examples of three DeFi attacks that remind you to keep your guard up.
$610-million loss from Poly Network
The most significant DeFi attack so far was on Poly Network in 2021, when hackers detected and exploited the vulnerability in contract calls of the network. Immediately, those hacking efforts resulted in a loss of more than $600 million in cryptocurrencies.
Poly made abundant communication and even published a despairing letter, starting with the salutation “Dear Hacker” and inviting the hacker to be its chief security advisor. Luckily, the hacker returned the stolen funds after three days, as they only desired to teach Poly a lesson.
Although the network remains in its position in the blockchain market, its DeFi security is under question.
$320-million loss from Wormhole
This February, attackers targeted the Wormhole network – the bridge between Ethereum DeFi projects and the Solana blockchain- exploiting its vulnerability for $320 million in cryptocurrency funds.
This heist has shocked the DeFi world.
The two Blockchain systems: Ethereum and Solana, were not the targets. Their underlying blockchain architectures are secure. Thus, hackers attacked the overlaying network Wormhole by minting new tokens on the side of Solana and draining the balance in Ethereum.
DeFi security lessons learned – Developers must enhance the security in DeFi blockchain bridges to avoid any possible attacks.
$182-million loss from Beanstalk
The DeFi project of Beanstalk lost 182 million dollars in a flash loan attack – 80 million pocketed by the criminals and the rest paid to execute the loan.
Accordingly, Beanstalk Farm uses voting power (determined by the token held) to accept loans. Thus, the attackers exploited the governance mechanism by conducting an urgent execution to steal reserve funds away from the liquidity pools.
Top 3 Common DeFi Attacks

The three case studies above are only some examples of DeFi attacks. Hackers find many ways to play the old trick – stealing your virtual money.
Price Oracle Manipulation
Oracles are third-party blockchain providers that offer real-world or external data such as statistics, weather information, or price feeds. Of all, the price feeds are the most commonly manipulated in DeFi attacks.
Attackers often penetrate the liquidity pools of DeFi systems through an oracle manipulation’s flash loan. Then, they sell the assets at a significantly lower price to attract perpetrators. Once the perpetrators repurchase the support, the attackers will excite the pool at a higher price.
Reentrancy Attacks
The case of the Poly Network is an example of reentrancy attacks.
Hackers attempt to drain out the balance of smart contracts as “if execution is paused in the middle of its running, entered again, and run completely without errors.” In other words, they turn the smart contracts into an ATM and take out money.
The Rug Pull
“Pulling the rug out” is a new scam of crypto attackers.
The hackers attract investments in their new DeFi projects yet delete their traces before the systems are built.
As scammers, hackers can control the DeFi protocol and even do away with liquidity. Technically simple and tremendously profitable!
Best Practices on DeFi Security

Undoubtedly, DeFi is one critical technology in current and future financial services. You can consider using it from now on, but only when you strictly follow these best practices.
- Update yourself on the latest knowledge of cryptocurrency and also DeFi technologies.
- Use decentralized and manipulation-resistant oracles to get full-market coverage and stay informed by fair price feeds.
- Improve smart contracts with special functions or whitelist particular external contracts to prevent interactions with unknown smart contracts.
- Carefully research the DeFi projects before you put money in, such as their traces, track records, experiences, etc.
- Ensure that your interactions are only through official channels.
Wrapping Up
Never put your DeFi security down!
Besides the golden rules above, you should remember that there is hardly a comprehensive list to cover all potential vulnerabilities. The more blockchain and DeFi grow, the more sophisticated attempts hackers create to exploit the systems and steal your money.
 4 minutes read
4 minutes read
