
Bug Bounty is a security program where businesses connect with a community of experts to find security holes in their products. For each bug found, the business will award a bounty to the bug-finder. It receives much attention from organizations thanks to its efficiency and cost optimization. So, what is Bug Bounty, how does it work? Let’s learn about Bug Bounty and its benefits to businesses in the following article.
I. Bug Bounty Overview
1. What is Bug Bounty?
Bug Bounty is a security program published by organizations, businesses, or 3rd parties. The purpose is to attract the community to detect and report security holes (bugs) in technology products where bonuses will be given to those who find bugs.
A standard bug bounty program will include 3 main parties:
- Bug Bounty Organizer: usually businesses, organizations, or 3rd parties. This is the organization responsible for designing & publishing the Bug Bounty Program, and also rewarding experts who find bugs.
- Products that need to find bugs: can be websites, mobile apps, IoT, API, computer software, service software – SaaS, …
- Experts: are the participants in the Bug Bounty program. They are cybersecurity experts, security consultants for organizations, pen-testers, white hat hackers, or a talented IT student.
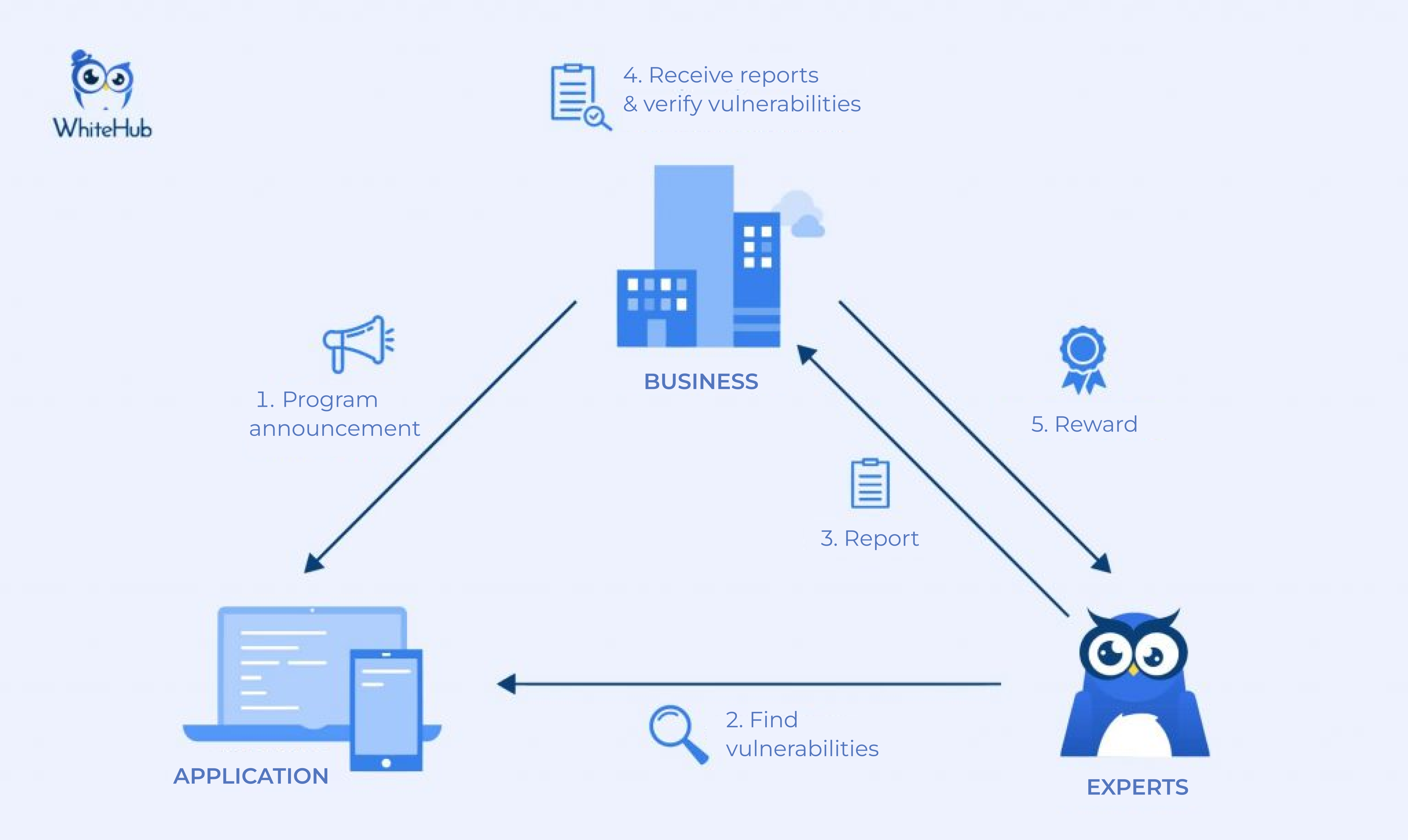
The rewards can be cash, certificates of merit, souvenirs, recognition, etc., but the most common is still cash. The bonus is more or less depending on the severity & impact of the security bug on users and businesses.
2. What is the effect of Bug Bounty?
The purpose of the Bug Bounty program is to find as many security holes as possible. And then fix those vulnerabilities before hackers find out. Bug Bounty helps prevent hackers from exploiting security flaws that lead to many unpredictable consequences.

3. What are Bug and Vulnerability?
Bugs are errors that cause a system, program, or software to function abnormally. Sometimes bugs also refer to errors that exist in the command line (code) of an application. In the Bug Bounty program, “bugs” usually refer to security errors (vulnerabilities). These are vulnerabilities or security weaknesses in systems, programs, and software. These flaws can be exploited by hackers and can cause many serious consequences. Vulnerability can arise at both the design and operational stages.
4. Bug Bounty Hunter
Bug Bounty Hunters are people who regularly participate in bug bounty programs to find bugs and get rewarded. They could be a pen-tester, white hat hacker, independent cybersecurity researcher, or an excellent Information Security student.
They love to find bugs and often participate in many different Bug Bounty programs to find security bugs. Both to satisfy their passion and to earn a significant extra income.
5. Penetration Testing
To be able to find security flaws, Bug Bounty Hunters need Pentest skills. This is a form of security testing for a technology product (web, app, API, IoT, etc.). This is the program where testers try to penetrate that product to detect security weaknesses that exist in the product. This is a technique used in Bug Bounty programs to find system security flaws. Testers are called Pen-testers.
6. Crowdsourcing trends
Unlike outsourcing, crowdsourcing utilizes community resources to complete a certain job (or part of the job). Crowdsourcing is often applied to jobs where the crowd proves to be more effective than a fixed group of people.
For example one of the most successful crowdsourcing start-ups is Waze. It is an application that warns of traffic jams and automatically chooses the best route. Waze allows users to send congestion information from anywhere to the data center. By processing this data, Waze helps app users choose the most suitable travel route. In this case, it is clear that the application would not be successful without the use of crowdsourcing.
The advantage of crowdsourcing is creativity, thus bringing efficiency and saving costs. This trend has been and is being applied to many different industries.
7. Crowdsourced security
Crowdsourced Security is the application of the crowdsourcing model in information security. It protects a technology product by finding vulnerabilities. Bug Bounty programs are part of the Crowdsourced Security solution. Also, there is a “Vulnerability Disclosure Program” (VDP). In this program, all reports from hackers are voluntary. Hackers may or may not receive a bounty for those reports.
The community includes pen-testers, white hat hackers, and freelance security researchers. They can be anyone who is passionate about security research: a software engineer, a system administrator, an ordinary IT worker, or a college student.
II. Benefits of Bug Bounty compared to regular Pentest service
1. More detected bugs
The work of finding bugs requires a lot of pen-tester skills, experience, and creativity. Therefore, the crowdsourced security model with hundreds or thousands of experts will bring greater benefits than the regular Pentest service consisting of only a group of experts (about 3-5 people).
Moreover, for most of the regular Pentest contracts, Pen-tester is under pressure about testing time. This partly affects their creativity when finding errors. In contrast, the pen-testers participating in the Bug Bounty platform are driven by rivalry and excitement. This mentality makes the work of finding bugs able to achieve more positive results.
At WhiteHub, the expert community has reached more than 1,400 professionals.
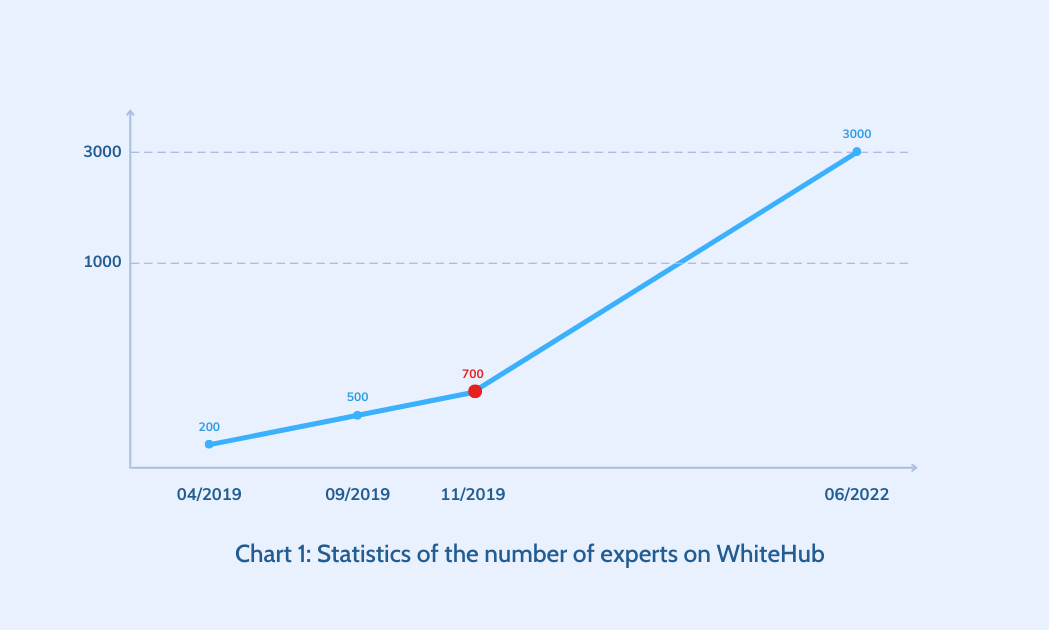
2. Cost saving
The cost of a traditional Pentest contract is usually fixed and depends on the reputation of each supplier.
- That makes the initial cost expensive, and not suitable for small and medium businesses, and startups.
- Sometimes the gaps in reporting don’t really add value to the business.
Through pay by vulnerability, Bug Bounty thoroughly solves the following problems:
- Enterprises plan budgets for the Bug Bounty Program. The cost of paying rewards for each type of vulnerability depends on the severity.
- Businesses will not have to pay when no bug is found, or if the errors are out of scope.
- The Bug Bounty program can be customized based on the budget plan of each enterprise.
3. Time flexibility
With traditional pentest services, pen-testers will perform tests for a fixed period of time (weeks or months) and then make an overview report. This can lead to delays in patching system vulnerabilities.
In contrast, Bug Bounty is flexible in terms of time. The Bug Bounty program allows each expert to submit a report as soon as they find the vulnerability. The advantage of the community is that each person has a different operating time frame, therefore reports will be continuously sent to businesses for timely processing.
4. Meeting the needs of continuous web and app development
The battle to attract users causes businesses to constantly update and improve their web products and mobile apps. Thus, security flaws can appear that the development department (dev) cannot predict. If every app update uses the pentest service, the costs will be too high. But if we use only automated security software, then it is not enough to ensure product safety.
A Bug Bounty program would be the perfect middleman solution. It allows businesses to freely implement the program, and choose when to activate the program to suit each stage of development at a reasonable cost.
The Bug Bounty program charges based on the results received. So if the update doesn’t create any vulnerabilities, the business won’t have to pay the fee. But if there is a serious vulnerability, the business pays for a realistic and worthy outcome.
Mr. Nguyen Huu Trung – Founder of WhiteHub Bug Bounty.
5. High customizability
Bug Bounty programs allow program owners to customize many features to suit their budget such as:
- Customize test coverage (public or secret).
- Customize the total budget and bounties for each bug.
- Select test coverage for the Bug Bounty program (public, semi-public, secret)
- Select testers (Limited to the best experts).
- Integrate vulnerability reporting into popular working software (Trello, Slack).
III. Popular Bug Bounty Platforms
Due to the difficulty of businesses in attracting many talented professionals to participate in the Bug Bounty program, third-party Bug Bounty platforms were born.
Bug Bounty Platforms are third-party partners that help businesses organize and attract talented security professionals. Bug Bounty platforms solve 3 problems:
- Help startups and SMEs access the expertise available on the platform instead of having to build a reputation and attract experts themselves.
- Create a playground for security researchers to exchange, learn, and earn extra income from passion.
- Solve the problem of organizing Bug Bounty professionally. Ensure the rights and privacy of both businesses and professionals.
Here are reputable 3rd party Bug Bounty platforms:
1. HackerOne
HackerOne is one of the most famous Bug Bounty platforms in the world. The company was founded in 2012 in San Francisco. As one of the oldest and most respected names in the industry, HackerOne connects businesses with the community of white hat hackers & security researchers through Bug Bounty and VDP programs. As of 2018, HackerOne’s white hat hacker network has reached 200,000 people.
Some typical customers of HackerOne include the US Department of Defense, General Motors, Starbucks, UBER, Spotify, Airbnb, Nintendo, WordPress, Snapchat, Twitter, and many other organizations and businesses.
2. Bugcrowd
Founded in 2011 in San Francisco, Bugcrowd is one of the most reputable units that help businesses announce the Bug Bounty program and attract testing experts. The company provides 4 services based on Crowdsourced Security, including Bug Bounty, Vulnerability Disclosure, Next Gen Pentest, and Bug Bash.
Bugcrowd is a security partner of many big brands like Tesla, Mastercard, Motorola, Atlassian, and Western Union.
3. WhiteHub
Launched in April 2019, WhiteHub is the first platform in Vietnam that connects businesses with security experts through the Bug Bounty program. At the end of Sep 2022, WhiteHub attracted more than 2500 security experts to participate in the platform, deploying Bug Bounty for over 100 domestic and foreign companies, in various fields such as eCommerce, Fintech, OTA, and SaaS, blockchain, etc.
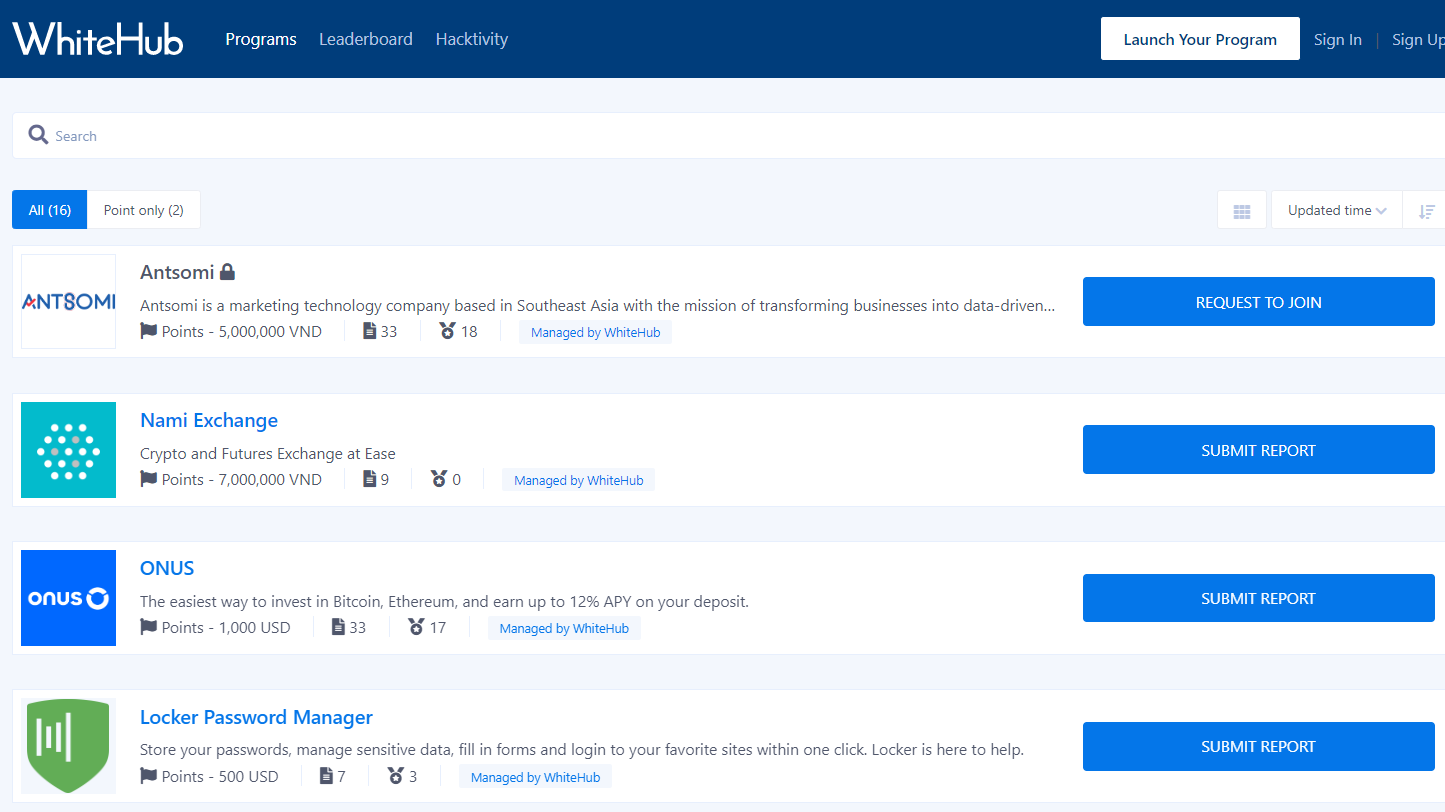
This is the Bug Bounty platform trusted and used by leading Vietnamese enterprises such as VinGroup (VinID), Giaohangtietkiem, Vntrip, Luxstay, Sendo, Finhay, and Getfly CRM.
“WhiteHub is a product of CyStack Vietnam, founded by a group of security experts with many years of in-depth experience and dedication to the industry. Our desire is to contribute to the development of Vietnam’s cybersecurity industry. Thereby, creating a driving force to promote the high-tech economy, helping businesses to take firm steps to reach further.”
Mr. Nguyen Huu Trung – Founder of WhiteHub Bug Bounty; CTO CyStack Vietnam.
Businesses are provided with the necessary tools to organize a professional and methodical Bug Bounty program. Thereby approaching the community of 1,400+ leading reputable security experts in Vietnam and in the region to find vulnerabilities in products.
Benefits:
- Security testing for websites, and mobile apps with a community of 1,400+ network security experts & pentester.
- More security vulnerabilities are detected at lower costs.
- Program information security with expert quality control.
 7 minutes read
7 minutes read
