
After we published the recent article about top security risks in SDLC, many readers were interested in the topic. They asked us to publish a detailed explanation of the secure software development life cycle.
And here is the second blog post on the series, which focuses on four points:
- What is considered a secure software development life cycle – SSDLC?
- Why should you employ a secure software development life cycle?
- Benefits of secure software development life cycle
- How do you ensure a secure software development life cycle?
When your eyes are landing here, we know you also want to learn more about the topic!
What Is Considered A Secure Software Development Life Cycle?
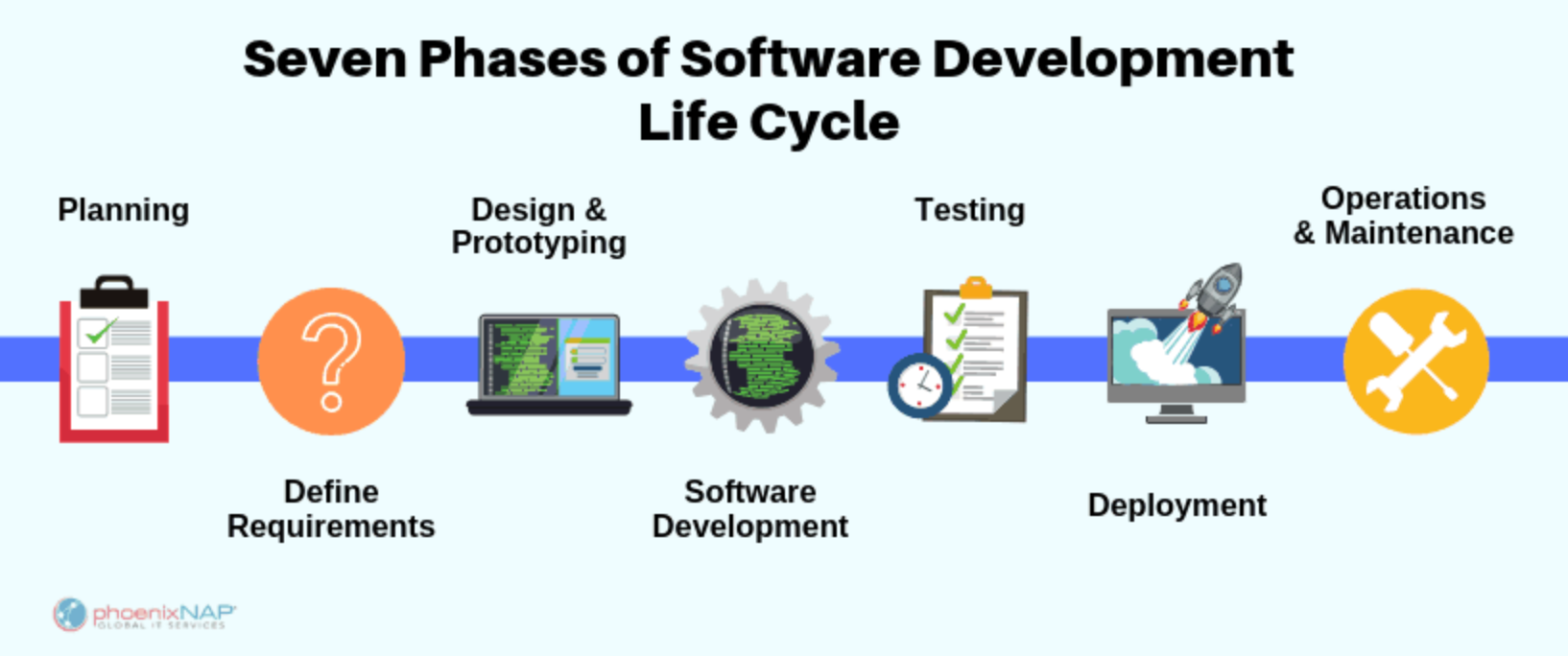
Simply put:
“Secure Software Development Life Cycle (S-SDLC) is a development approach in which developers must always be mindful of possible security risks in all development life cycle phases; then incorporate security artifacts from planning to operation maintenance.”
Why Should You Employ A Secure Software Development Life Cycle Important?
S-SDLC framework has become increasingly important due to the rise in security risks during a software project and the low response of the traditional software development life cycle.
Back to a couple of decades ago, the primary approach to software development is the Waterfall model. The application’s life cycle is linear-sequential, meaning each phase must be finished before the next step begins. No overlapping is allowed.
All requirements, including security, are highly specified in the first place and laid the groundwork for the rest phases.
However, security risks are complicated and challenging to predict clearly in advance. Let alone the current world has many interconnections that criminals or nefarious users target at any time. When the security issues are addressed in the testing phase of the Waterfall model, the potential vulnerabilities might have been exploited for quite a time. Then, it requires significant effort and resources to fix them right.
Nowadays, many developers have switched to another development approach: Agile. This approach allows splitting up an extensive software application into multiple mini-releases. Agile offers improved flexibility and frequent testing of functions and security in all phases. Issues, if any, will be predicted and detected soon.
Benefits Of Secure Software Development Life Cycle

Secure software development is inevitable and vital, as mentioned above. In return, secure SDLC also significantly benefits the success of software applications.
- Enhance the responsibilities of the development team as a whole
It is critical to make security an ongoing concern in any software development.
Since security requirements are applied to all phases, they keep stakeholders of the software project on the same page about security issues. They have to take part in and have responsibilities for the application to be protected without delay.
- Reduce cost and effort in fixing security issues
Back in the time when the development teams often implemented security-related tasks during the testing phase, it was very late or even not at all to discover issues.
Unfortunately, IBM confirmed that it took 15 times more to fix bugs detected while testing than those found during the design phase. Thus, the earlier the team can maintain security tasks during the software development life cycle, the cheaper they have to pay.
- Build trust in the client and customers
According to the S-SDLC, all software project stakeholders are included in the security considerations. Your client and end-users, therefore, have a good impression of your business.
In contrast, if your software is not secure enough, you put their information at risk of attacks.
How To Ensure Secure Software Development Life Cycle?

As advantageous and critical as the secure software development life cycle, all development teams strictly follow the best rules in their activities.
Build a secure software development policy
Since security risks are hard to predict and prevent, development teams must create a security baseline. It is a set of guidelines to detail the security procedures and practices to reduce vulnerabilities during a software life cycle.
For instance, the policy includes instructions on how to view, assess, and demonstrate security in specific phases. There is also a discussion on the risk management approaches and necessary processes to protect your software application (separation of environments for developing, testing, and operating.)
The policy will work as a vehicle for managers of the development team to implement a secure software’s strategic methodology. Once the policy is applied, the engineering team must also create a gap analysis to contrast the practical activities in the software development life cycle against the baseline. If a gap exists, it needs addressing in the early phases to reduce the efforts and expense.
You must also build a checklist to closely and frequently monitor the policy and keep them updated and enhanced. If possible, some development organizations have security experts evaluate and create a plan for a secure software development life cycle.
Continuously train the developing teams on the policy
Organize training sessions for the teams, including developers, architects, designers, testers, etc., to update them on the above policy. Each team member must understand their duties and strictly perform their daily tasks. In addition, security awareness also targets other stakeholders involved in the project and the organization.
Most sessions are firstly traditional theoretical classrooms. They help equip the stakeholders with security software development life cycle policy. However, it is recommended to narrow the critical security points in slides or records in advance so that attendants can have brief yet practical knowledge. Examples of common security risks and solutions need to be included.
Next, conduct exercise training to assess how well the stakeholders intertwine the theories with their practice environments. There must be experienced mentors who can on-job review and instruct the trainees during the cycle.
Pick up an S-SDLC framework to guarantee consistency
Since secure software has become a norm, experts have built many frameworks to help enhance security. Then, the development team can choose a specific framework to align their practices throughout the software development life cycle.
Of which, we suggest using the framework of NIST (SSDF). This framework includes a set of sound, fundamental, and secure practices for software development, referring to the S-SDLC of OWASP, BSA, and SAFECode. With those practices, organizations can significantly reduce vulnerabilities and the potential exploitation of undetected vulnerabilities and address the root reasons for security issues to prevent their recurrences – following four stages.
- Firstly, prepare the organization (PO) by ensuring that its people, technology, and process are prepared and enhanced towards secure software development, either at the project or organizational levels.
- Secondly, protect the software (PS), including all components, from unauthorized and tampering access.
- Next, produce well-secured software (PW), so there are a minimum number of vulnerabilities once releasing the software.
- Finally, respond to vulnerabilities (PV) appropriately to address the root causes and prevent the vulnerabilities’ recurrence in the future.
Every practice of the SSDF is outcome-based and contains tasks, implementation examples, and references.
- Practice: The practice is a brief statement with an explanation and its unique identifier to determine the definition and benefits of the practice.
- Task: Individual action(s) are required to complete a practice.
- Implementation example: The example indicates a given scenario helpful to demonstrate the practice.
- Reference: It is a secure practice document and how it maps to a particular task(s).
Apply the framework to the software development
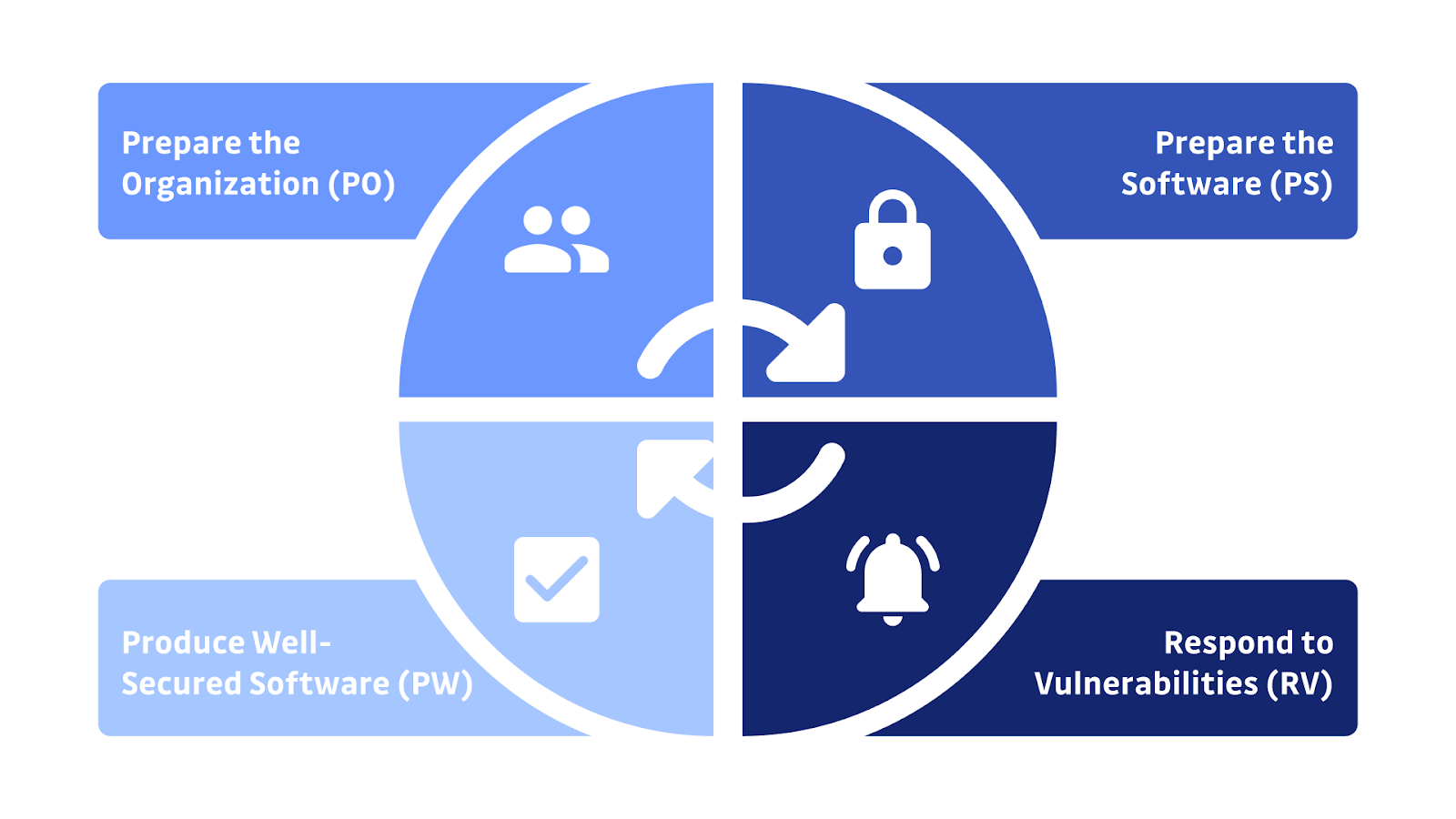
We break down the four stages for reference if you use the NIST (SSDF) framework.
PO: practices, tasks, and examples
The preparation involves defining internal security requirements (policies and risk management approaches) and external requirements (laws, regulations, etc.)
Next, assign the software requirements roles and tasks so the development team can prepare role-specific training sessions and supporting tools. Tasks include information on identifying, communicating, and maintaining all security requirements throughout the life cycle.
Finally, define benchmarks to take notes of security standards achievements.
Examples of preparing the organization:
- Defining software development specifications such as architecture requirements and coding practices for developers.
- Agreeing on reviewing and updating requirements yearly or mainly after incidents.
- Assigning roles and training plans and preparing to update roles at any time.
- Specifying toolchain categories and relevant tools, then incorporating automation for the operation and management of the toolchain.
- Building an audit trail to keep track of SDLC-related actions.
- Determining KPI (key performance indicators), using an automatic toolchain to collect feedback, and reviewing and documenting a security checklist to achieve defined standards.
PS: practices, tasks, and examples
It is paramount to protect code and enhance the integrity of software from the first phase until it reaches the end customers. The developers must safeguard the code from tampering and unauthorized access, following the least-privilege principle.
Examples of protecting the software practices:
- Storing the code in restricted-access and secure repositories
- Using version control to track all changes in code
- Publishing cryptographic hashes used for released software
- Only using trusted authorities for singing code
PW: practices, tasks, and examples
When producing well-secured software, the teams go through many steps involving various practices and actors.
The application is under review to align security requirements before the team evaluates third parties’ compliance with these requirements. Within time, the team reviews and tests all code using automated and manual means. Meanwhile, developers must follow best practices in writing codes and configuring the developing process. In the end, configure secure default settings to protect the software out of the box.
Examples of producing well-secured software:
- Educating the team about secure developing best practices and risk assessment techniques
- Lesson-learning from previous releases to address as many potential risks and security requirements as possible
- Stating requirements of secure software development life cycle in 3rd-party contracts and policies to manage their risks
- Only developing the software in environments mandating safe coding practices
- Implementing peer reviews, penetration testing, and dynamic/ static analysis testing to scan all underlying vulnerabilities, then documenting results
- Establishing a repository of reusable trusted developing components
- Testing all approved default configurations of security
RV: practices, tasks, and examples
Vulnerabilities are still possible even if the development team strictly follows the secure software development life cycle.
When there is a vulnerability, it is essential to fix the issue and gather data to prevent future recurrence. The vulnerability is prioritized to reduce the window of threat.
Examples of responding to vulnerabilities:
- Building reporting and response program to a vulnerability
- Implementing automation to scan vulnerable data and code analysis
- Predicting the impact of the vulnerable and preparing resources to fix the issue
- Detecting the root causes and documenting the lesson-learn for future detection and prevention of recurrence
A Summary Of The S-SDLC Best Practices
The framework above covers almost all secure software development life cycle best practices. We want to summarize them and include other techniques for you to take away:
- Think about secure software development from the beginning
- Create a transparent policy and keep all members frequently educated and updated on that policy
- Employ a consistent framework for secure software development, for instance, the NIST’s SSDF)
- Develop the software following the best practices and aligning to security requirements
- Secure the code integrity against any possible tampering and strictly regulate all contacts with the code
- Apply an early and frequent review and test on the code to examine any flaws and catch vulnerabilities
- Get prepared to mitigate the detected vulnerabilities in real-time and update the software to narrow down the window of exploitation attempts
- Add secure default settings to the software’s function list
- Use action checklists to keep track of security policies and procedures within periodic intervals: weekly or monthly
- Stay proactive and agile on best practices, so the teams can stay ahead of what is coming and be well-prepared
Final Words
We know that applying the above practices for a secure software development life cycle requires a serious investment of efforts and resources. However, it will all begin by thinking with a security-first approach. Do not hesitate to note down the practices, and let us know if you have any concerns.
 8 minutes read
8 minutes read
