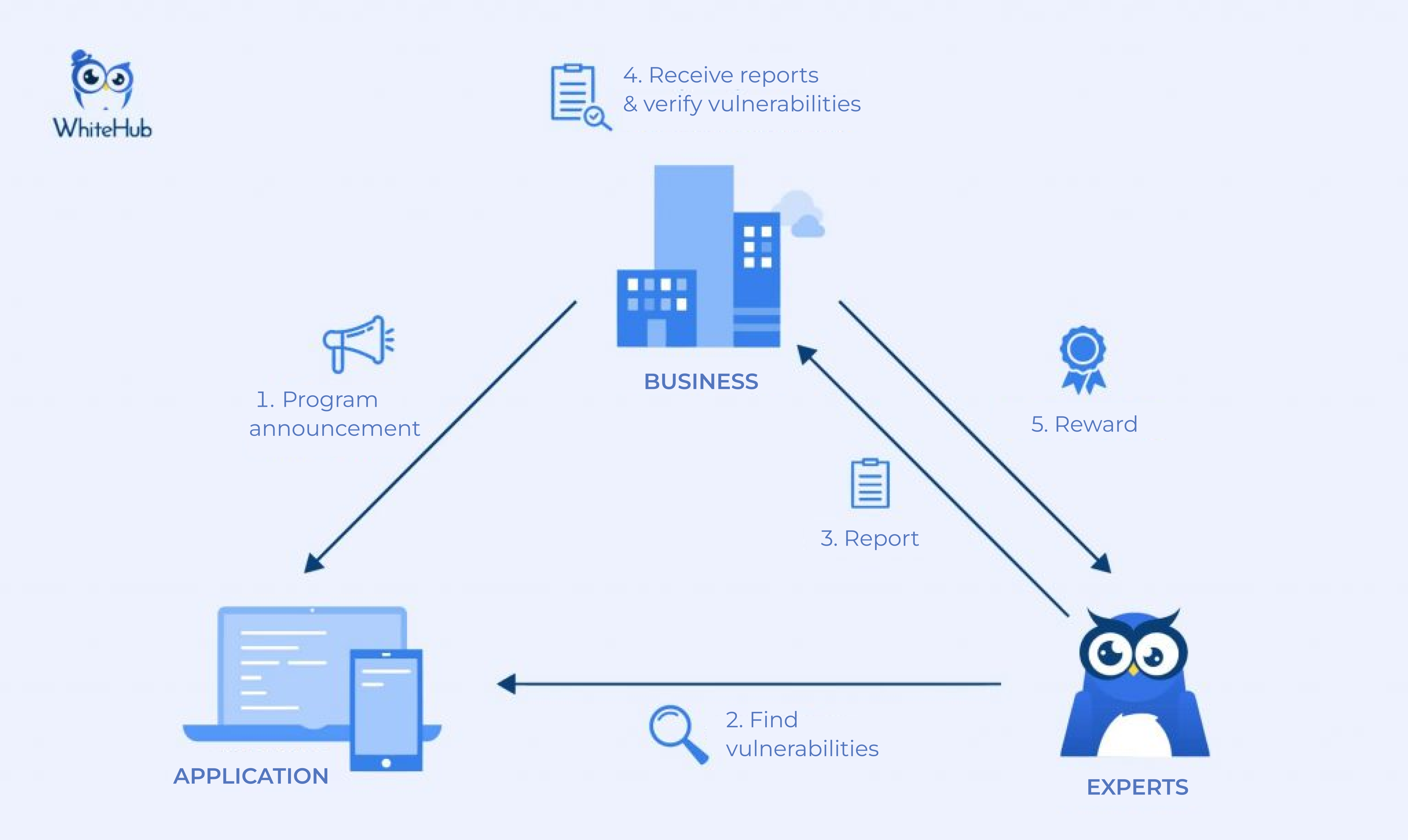
Because DevOps environments are very dynamic and applications are deployed continuously, the product life cycle becomes shorter, resulting in a higher rate of security vulnerabilities. No business wants hackers to break into the application system and steal important information or customer data. That’s why businesses should integrate Crowdsourced Security into the Software Development Life Cycle (SDLC).
Maximum software security at every stage of development
Continuous code review
An effective community security testing program is ongoing and involves a non-stop cycle of steps: evaluation, planning, and improvement. Crowdsourced Security provides security and programming teams with resource flexibility and scalability.
Unlike internal QA, security researchers are constantly innovating attack methods and approaches. They are incentivized to hunt down attack vectors with a higher potential for damage.
Continuous and efficient feedback
Vulnerabilities are prioritized based on their impact on businesses, carefully documented, and validated so developers know what and where to look. This feedback loop helps security teams gain insights and can effectively and efficiently patch issues discovered by the research team. The integration with Jira, Github, ServiceNow, etc. enables secure feedback directly to developers’ native tools, saving time and effort.
Continuity
Typically, Crowdsourced Security implementers also provide step-by-step instructions and industry-standard resources, making it easier for developers to successfully patch and strengthen the codebase. This makes the product development process seamless, without interruption because of harmful security flaws.
Meeting the needs of imperative product completion
Agile has brought significant progress: iterating faster and software quickly adapting to business needs. However, as each code changes, the vulnerability increases. It is unrealistic to think that a limited – resourced security team will be able to uncover all the vulnerabilities in new software, especially at today’s pace of innovation.
Currently, companies are focused on developing products and applications to drive revenue, but limited security resources put it all at risk. Developers are encouraged to push the product out as quickly as possible; however with deadlines and features requested, security often becomes a low priority issue. This is not the fault of the programmers. This is the fault of an unbalanced and outdated security model.
Conclusion
Integrating Crowdsourced Security with your SDLC is an efficient approach, which can be scalable. Crowdsourced Security provides access to thousands of independent security researchers. These skilled and well-intentioned hackers bring a range of skills to more quickly identify and report high-priority vulnerabilities to your team. Through Crowdsourced Security, you get peace of mind by constantly testing your apps. Furthermore, since only valid errors are rewarded, the cost of these outcomes is also very efficient.
 2 minutes read
2 minutes read
