Leaders might not afford to miss our article on cybersecurity tips.
Every day, around 30,000 websites worldwide are hacked, and they cost up to trillion dollars annually. In other words, if your business has any connection to the Internet, it will likely become a hacker’s target and suffer significant financial consequences.
Don’t let your guards down!
What Is Cybersecurity?

The most simple definition of cybersecurity is keeping the information of individuals or companies secure in the cyber world.
Or to understand it in more detail, cybersecurity is a set of disciplines and practices to defend any internet-interfered devices against nefarious attacks such as data breaches, identity theft, phishing scams, ransomware attacks, and financial losses. Those attacks are often attempts by cybercriminals, hackers, and spammers.
Applications of cybersecurity; however, are challenging due to numerous reasons (namely but not limited to):
- Failures to consider your business as a vulnerable target
- Lack of training for employees about cyber threats
- Increase in types of cyberattacks: ransomware, phishing, etc.
- Missing security patches to address vulnerabilities.
- Shortage of corporate security programs and backup plans.
Fortunately, this article recommends the best cybersecurity tips to address the above problems.
Top 9 Updated Cybersecurity Tips for Leaders
#1: Think Like a Leader

Big-tech leaders in Amazon, Google, Apple, Microsoft, and Facebook have a cybersecurity mind; thus, they have invested nearly $2400 million in enhancing their systems against cyberattacks.
These leaders consider cybersecurity a strategic business-enabling function rather than a mere supporting function. It is believed to directly impact branding, revenue, stock value, customer relations, etc.
You should also think like them and integrate cyber risk management into your business.
#2: Foster Internal & External Partnerships

A business needs to work with various internal and external partnerships to share essential information to detect potential cyber risks and solve the consequences of attacks if any.
As a cybersecurity leader, you must develop an agreed and shared vision, objectives, and key performance indicators among partnerships to deliver highly-secure practices.
#3: Develop And Apply Enhanced Cyber Hygiene

Cyber hygiene is a part of cybersecurity. It is a set of routine actions of businesses to secure users, networks, devices, and sensitive data from attacks and thieves, following five principles:
- Secure the active directory, such as the Administrative Tier Model of Microsoft.
- Build a configuration management system and detailed inventory.
- Establish a patching strategy that automatically scans potential vulnerabilities of the environments and alerts the businesses.
- Run a robust business-wide authentication.
- Improve mechanisms for data security and business processes.
#4: Protect The Access to Critical Assets

The rule of thumb is least-privileged access, meaning users do not have equal privileges.
Cybersecurity leaders must define roles and permissions for every user to access organization information. It is also required to develop identity and access management policies, so users know exactly their roles and disciplines if they breach unauthorized access. For instance, a project developer cannot access financial data; a finance manager cannot access the code repository.
#5: Avoid Phishing by Protecting Your Email Domain

Email is the number 1 attack vector of cyber criminals, and 90% of attacks on businesses start from malicious emails. Thus, protecting your email domain from mitigating email abuse will be secure.
Here are some email cybersecurity tips:
- Educate all employees to recognize phishing emails.
- Filter and quarantine spam emails and malicious content.
- Employ anti-malware software on all endpoint devices.
- Comply with cyber-hygiene solid tips. Stay updated on new phishing scams to plan solutions.
#6: Apply a Zero-Trust Approach
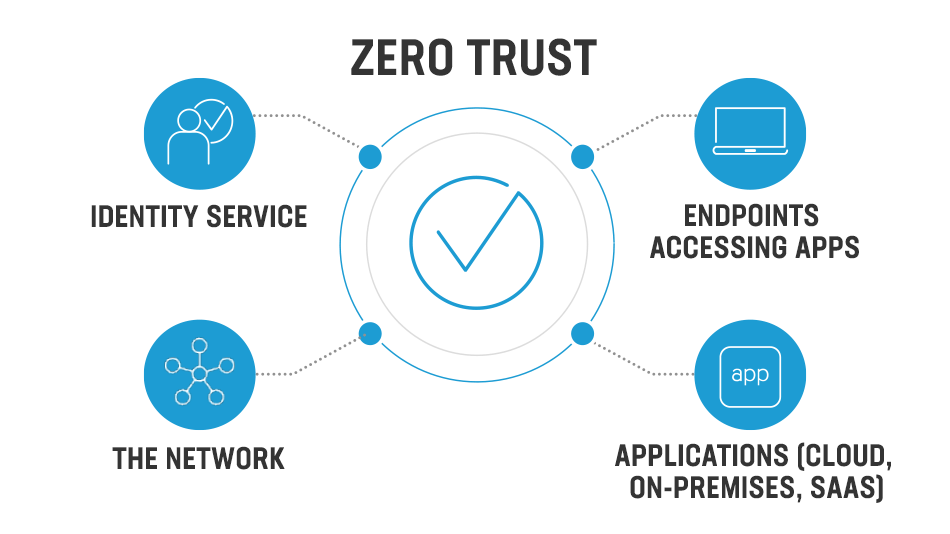
The Zero Trust framework implies that every business eliminates implicit trust and requires all internal and external users to be authenticated and authorized continuously, following six steps:
- Restructure user access according to their needs.
- Review due diligence using the backgrounds of vendors.
- Understand existing cybersecurity practices of vendors.
- Bind vendors with security terms and standards in contracts.
- Audit 3rd-party vendors following the business practices.
#7: Prevent, Detect, and Respond to Cyber Risks

Leaders should develop a Threat Intelligence team to proactively hunt through the infrastructure of the businesses to detect potential cyber risks and quickly respond when the risks become issues.
We suggest a Mitre Attack framework in three steps:
- Prevent: It is recommended to apply multi-protective layers on critical assets and mitigate the risk of intrusion.
- Detect: Cyber threats keep evolving; thus, prevention is not perfect. Prepare for attacks to happen but invest in adequate detection mechanisms.
- Respond: Once your business detects or accidentally suffers from a cyber breach, be calm first. Next, respond timely and effectively to minimize possible impacts. Then, enhance the existing cybersecurity system for future incidents.
#8: Prepare Crisis Management Plan
Cyberattacks often target customer databases of businesses and exploit them illegally. Thus, companies are to blame for not securing the data carefully. This is when a crisis starts.
A Crisis Management Plan is the next cybersecurity tip for leaders. Timeliness, transparency, and simplicity are essential to establishing a trusted relationship with stakeholders: customers, investors, regulators, etc.
#9: Develop a Robust Disaster Recovery

If you follow the tips above, we are sure that the impacts of cyberattacks will be minimized significantly. The next step is to recover as quickly as possible after the disaster.
Keys to suggest:
- Define your business’s critical assets
- Determine means of recovery
- Call the governance for help (if urgent)
- Review and practice cybersecurity tips regularly
Final Words
Are you a cybersecurity leader?
If yes, you must understand the importance of a secure environment and risk awareness, then integrate cybersecurity into every business task.
Our cybersecurity tips are valuable references for you!
 5 minutes read
5 minutes read
