In this article, we will learn what Cybersecurity Framework is, and why it is necessary for business network security. We also learn how common network security models like ISO 27001, NIST model, or PCI DSS security standards are different from each other. At the same time, the article also helps you outline a strategy to build an appropriate security model.

Recently, cyberattacks are becoming increasingly sophisticated. That is why businesses across the globe are looking for ways to protect their information networks from these attacks.
IT teams are actively looking for new ransomware and exploits that are at risk. But can they completely defend against all of these unpredictable attacks?
The answer is definitely “No”.
That is why it is necessary to take a timely approach to mitigate the consequences of attacks. With proper cybersecurity measures, businesses can protect themselves from becoming a victim of hackers.
To be able to do that, businesses should implement the Cybersecurity Framework (network security model). A good framework will help them strengthen their security wall and always stay in control of the situation.
In this article, we will learn what Cybersecurity Framework is and why it is necessary for business network security. What is the strategy, its benefits, and how to implement it.
What Is a Cybersecurity Framework?
The Cybersecurity Framework is a set of pre-existing policies and procedures developed by leading cybersecurity organizations. Its purpose is to strengthen cybersecurity strategies in the business environment. These are proven theoretical knowledge and practical procedures.
These models are often built for a specific industry to minimize unnamed configuration errors that exist in the information network of the enterprise.
To simplify, Cybersecurity Framework is a pre-designed model to enhance information security for your business.
Why Is The Cybersecurity Framework Important?
A good security model will upgrade your existing security protocols and establish new layers of security if your previous system did not have one.
These models will also help businesses define what their security standards are, and how to strengthen them.
All of the models below are carefully designed and tested in real life under many different situations. So you can rest assured to consult these models.
Strategies For Building A Security Framework
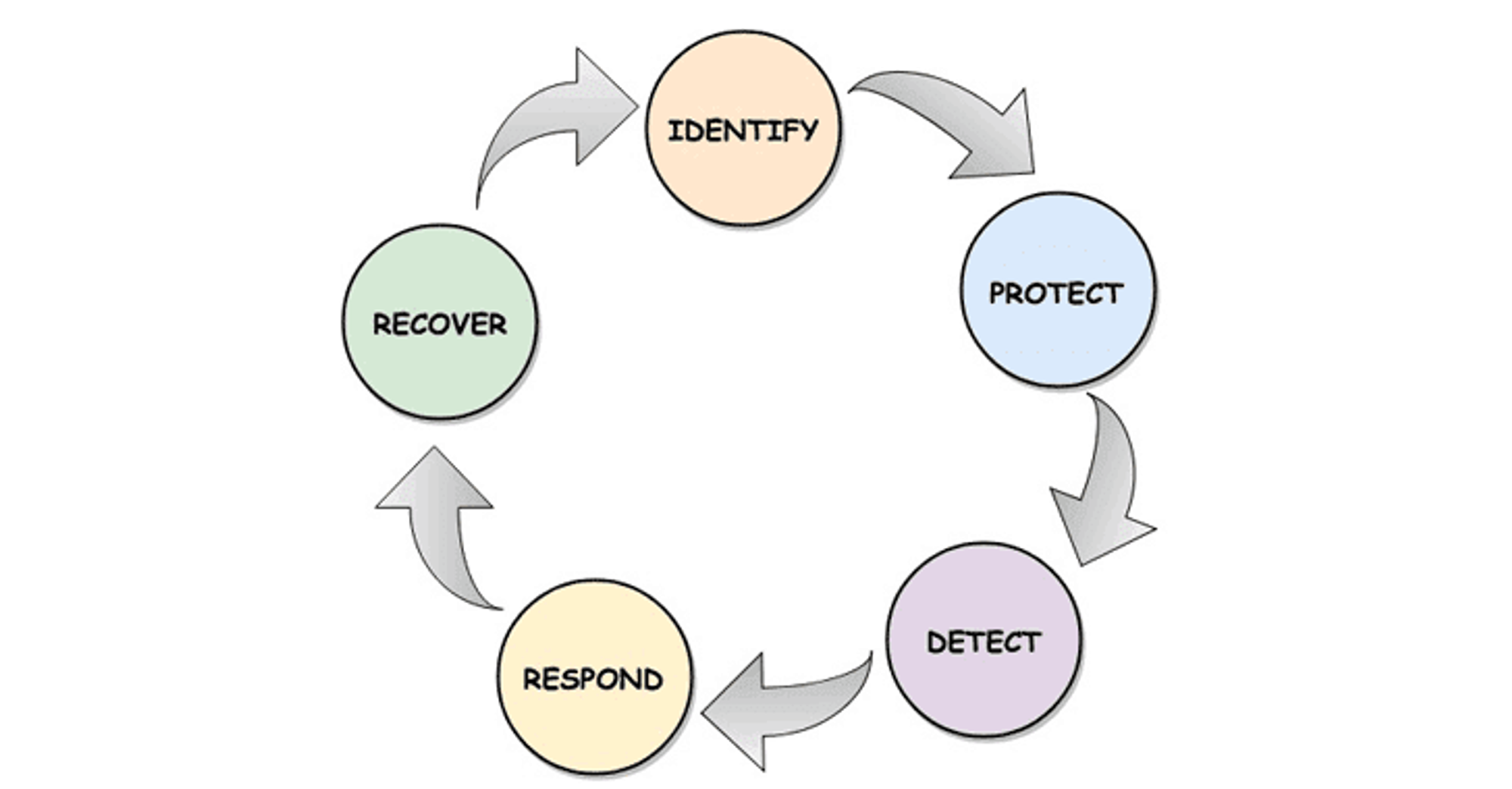
There are five steps that make up a Cybersecurity Framework: Identification, Protection, Detection, Respond, and Remediation. Any network security model can apply this process.
Here are the details of each step in the process:
- Identification
This step helps businesses identify network connection points in the business environment. It can be information technology devices, resources, information, etc.
- Protection
This step is to strengthen the process of access control, data security, and maintenance in and around the business environment. It can be understood as a proactive phase of problem-solving in network security.
- Detection
This step is when businesses will find and detect potential vulnerabilities by monitoring logs and intrusions at the network and device levels. They will carry out both operational management and security information.
- Respond
Once a vulnerability has been discovered, businesses need to respond quickly. Understand the vulnerability, fix the flaws, and move forward with the remediation process.
- Remediation
Remediating the cybersecurity process, as well as troubleshooting and contingency planning will be handled during this phase.
Common Security Framework
ISO 27001/27002
The International Standards Organization (ISO) developed ISO27000. It is a framework that covers all broad aspects of cybersecurity which is applicable to all sectors.
This framework is compared with the ISO 9000 standard in production. Helping businesses define and measure the quality of cybersecurity in their environment.
While ISO2700 is an overview framework, ISO27001 focuses on conditions and ISO27002 focuses on implementation.
All of these frameworks are public to help businesses apply them in their own networks.
In addition to the above standards, there is also ISO27799. It is a security framework for the healthcare industry.
CIS Security Control
The Center for Internet Security (CIS) has designed a set of key security controls. These controls are crucial for businesses to implement in their networks to achieve an efficient network.
CIS has developed three sets of critical security controls for the business. Including 20 controls, they are all fundamental and organized. These methods can perform many of the security controls required for a business environment.
Businesses need to implement these 20 control methods to have a long-term sustainable security system. If it is not possible to implement all of them, at least half of them should be applied.
NIST Model
The US National Institute of Standards and Technology (NIST) has also published similar policies and rules. Their audience is governmental organizations to develop methods of effective information security.
The NIST model can also be applied to other industries. Controlled Unclassified Information (CUI) will also be the main object of this model.
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) is a cyber security model. It is designed to strengthen the security of payment accounts by protecting electronic transactions such as credit cards, debit cards, and cash cards.
All of the above models are built, validated, and the public to ensure businesses will follow industry standards and implement effective security.
Implementation Steps
After determining the right cybersecurity model for the business, the implementation process needs to be followed according to the guidelines. Here are some steps to take to start and maintain this process.
- First, businesses need to check and determine their current security situation
- Analyze ongoing projects, processes, and resources associated with those projects
- Understand cybersecurity models by studying related documents
- Determine what security controls have and have not been implemented in the network
- Identify which security layer is unstable and plan to fix it
- Implemented within a defined period for easy monitoring and management
- Mark control methods that have higher efficiency in the model
- Discuss the entire plan with key stakeholders, including all stakeholders, and move to implementation
- Continuously monitor the execution process
- Regularly reports and hold meetings to measure challenges
- Record the entire process for monitoring, inspection, and other purposes
The Cybersecurity Framework plays a key role in fortifying and responding to unexpected cyber scenarios. It helps keep businesses from falling victim to cybercrime.
Businesses need to clearly understand the requirements they need to meet. They also have to analyze the entire implementation process after discussing with stakeholders and the IT department.
Advantages Of Cybersecurity Framework
- Save effort: Available Cybersecurity Framework helps businesses minimize research efforts while ensuring strict security standards.
- Enhance network security in the organization
- More effective data security
- Easy to manage and monitor
Disadvantages
- The execution process can take days, affecting work performance
- Improper implementation can cause security flaws
- Can be costly
Conclusion
Nowadays, cyber attacks are becoming more and more sophisticated. Thus, businesses should adopt the right Cybersecurity Framework to build a solid defense against hackers.
Deciding to build a framework is 50% successful in complying with security standards. However, that model must be maintained to produce the expected results for the network security system of an enterprise, thereby securing the information of businesses and customers.
 5 minutes read
5 minutes read
