On December 3, 2025, the React development team issued a critical alert regarding a severe Remote Code Execution (RCE) vulnerability within React Server Components (RSC). This flaw allows unauthenticated attackers to execute arbitrary JavaScript code on the server. Designated as CVE‑2025‑55182 and dubbed “React2Shell,” this vulnerability carries the maximum CVSS v3 score of 10.0.

Context
React, originally developed by Facebook, is a cornerstone of modern web development, widely used for building highly interactive User Interface (UI) components. A key feature of its modern ecosystem is React Server Components (RSC), which allows parts of a React application to run on the server and stream results to the browser to optimize performance. It is this specific component that lies at the heart of the vulnerability.
The security risk was first identified on November 29, 2025, by researcher Lachlan Davidson, who promptly reported it to the teams behind React and Next.js (a leading web framework built on React). By December 3, 2025, both development teams had released emergency notifications and patching guidelines to mitigate the risk.
Anatomy of the Vulnerability
CVE‑2025‑55182 is fundamentally an insecure deserialization vulnerability in how React Server Components handle data.
An unauthenticated attacker can craft a malicious HTTP request and send it to any Server Function endpoint. When React attempts to deserialize this request, it triggers the execution of arbitrary code on the server (RCE). Detailed technical specifics are currently being withheld until a sufficient percentage of the ecosystem has applied the patch.
Key Mechanics:
-
Payload: The attacker creates an invalid data packet that forces the server to execute the code embedded within the payload during the deserialization process.
-
Access: Because RSC is frequently enabled by default, applications can be compromised even if they have not explicitly implemented server functions.
The name “React2Shell” was chosen by researchers to evoke Log4Shell, signaling a vulnerability of comparable gravity in the security world. As of this update, there are no confirmed public reports of this exploit being used in the wild to bypass default configurations, nor have reputable security firms confirmed active compromises.
The Widespread Impact of React2Shell
React2Shell is being assessed as one of the most critical vulnerabilities of recent years because it violates a foundational principle of software security: server-side code must never be controlled by user input.
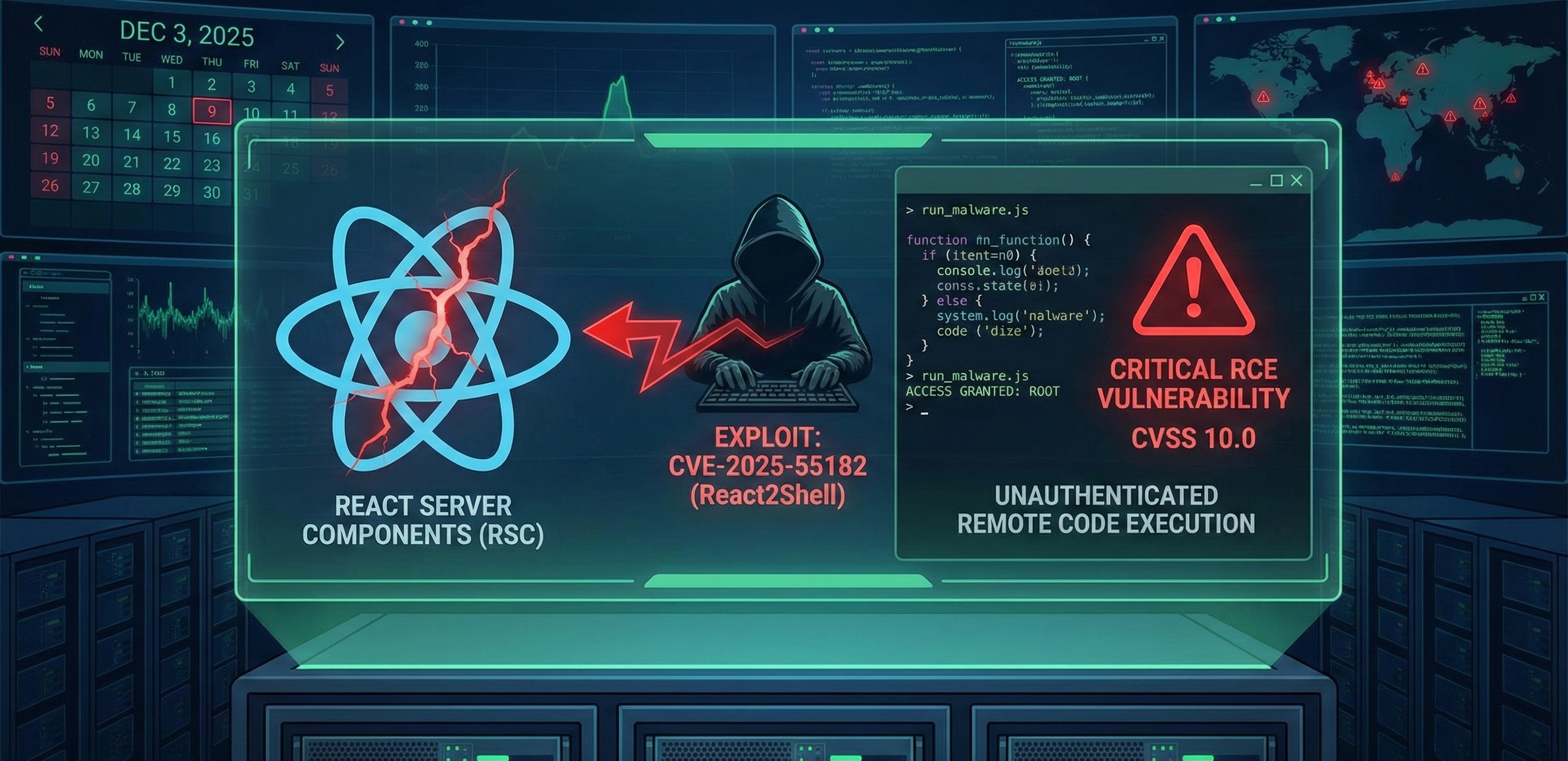
In the modern web landscape, the combination of remote access, no authentication required, zero-click execution, and server-level control represents the highest tier of risk.
-
Ubiquity: According to the “State of JavaScript 2024” survey, 82% of developers use React.
-
Ease of Exploitation: With RSC enabled by default in many frameworks (most notably Next.js), a minor configuration oversight can expose a production server.
-
Consequences: Successful exploitation allows attackers to steal sensitive data, manipulate application logic, or install persistent malware.
React is the engine behind countless platforms, from e-commerce and SaaS dashboards to financial systems. Many development teams may not even realize they are utilizing the affected solutions due to the default behaviors of their frameworks.
Mitigation and Recommendations
The ease of exploitation necessitates immediate action. React2Shell puts not just the website at risk, but also the backend infrastructure—including databases, internal APIs, and cloud services. While Next.js has issued its own warning, the root cause lies within React’s server packages.
CyStack recommends that organizations immediately inventory all services dependent on these packages, including microservices, serverless functions, and other backend workloads.
1. Immediate Library Update
The most effective countermeasure is to upgrade to the patched versions of react-server-dom-* immediately:
-
Versions: 19.0.1, 19.1.2, or 19.2.1.
-
For Next.js users: Ensure you upgrade to the specific patch corresponding to your organization’s version branch.
-
Related Ecosystems: Check for updates from associated frameworks such as React Router, Expo, Redwood SDK, and Waku.
2. Implement Interim Defense Measures
For applications that cannot be patched immediately, deploy the following defenses:
-
WAF & Reverse Proxy: Configure Web Application Firewalls to detect and block suspicious payloads targeting RSC endpoints.
-
Monitoring: rigorous monitoring of logs for abnormal HTTP requests.
-
Vulnerability Scanning: Utilize tools like CyStack VulnScan or similar comprehensive scanning solutions to identify exposed assets within your infrastructure.
3. Monitor Vendor Advisories
Stay vigilant regarding updates from the React and Next.js teams. Note that security databases may consolidate the Next.js CVE into the main React CVE, so vulnerability management tools might only display CVE‑2025‑55182.
Conclusion
The React2Shell vulnerability underscores the critical importance of secure data serialization and highlights how deeply modern JavaScript frameworks impact backend security. While no active exploitation has been recorded as of early December 2025, the severity, ease of attack, and ubiquity of React dictate that organizations must not wait.
Upgrade to the latest patched versions, review your RSC usage, and implement temporary protection layers to minimize risk. Stay updated with vendor notifications and remain ready to respond to any signs of exploitation.
Huy Nguyen
Security Expert of CyStack
 4 minutes read
4 minutes read
