Introducing from CyStack:
Next-Gen Penetration Testing
Proactively identify security gaps by simulating realistic cyberattacks, and patch them before malicious actors. Manage system flaws using a real-time dashboard, ensuring vulnerability oversight and zero-latency collaboration.




The meaning of security has evolved
“The Global Risks Report 2024” from the World Economic Forum identifies cyber insecurity as a leading global threat, with noticeable trend: attackers leverage AI to enhance their operations more swiftly than defenders can reinforce their defenses.
Organizations can no longer rely on static approaches, but relentlessly validate their own defenses through offense testing.
WEF - Global Risks Report 2024
However, traditional Pentest is
costly and slow to implement
Mối đe dọa về lỗ hổng bảo mật luôn tiềm tàng và tăng rủi ro cho doanh nghiệp của bạn

30.000+
new vulnerabilities discovered every year

100x
vulnerability remediation cost after development periods

~277 days
for an organization to detect a security vulnerability
Fortinet, Functionize, SentinelOne
Our Next-Gen Pentest services
offer you the best ROI package

50% cost
saving compared to traditional Pentest offering1
1 Based on our internal benchmarks.
5x faster
than traditional Pentest methods
100%enterprise-grade quality
& standard compliancecompared to top-tier security companies
Your business assets undergo CyStack’s
comprehensive 5-Step testing process
A globally recognized 5-step framework executed by elite pentesters to pinpoint vulnerabilities with speed and precision
01/ Threat Modeling
- Identify high-risk assets and potential attack vectors based on the MITRE ATT&CK framework.
- Map critical systems and uncover hidden attack surfaces.
- Prioritize threats and define the testing scope to maximize efficiency.

Testing everything is inefficient - we focus on what attackers will actually target.
01/ Threat Modeling
MITRE ATT&CK Tactics in the Enterprise Matrix
02/ Vulnerability Analysis
Detect security weaknesses based on OWASP Top 10 & CWE standards. Prioritize remediation based on exploitability and impact severity.
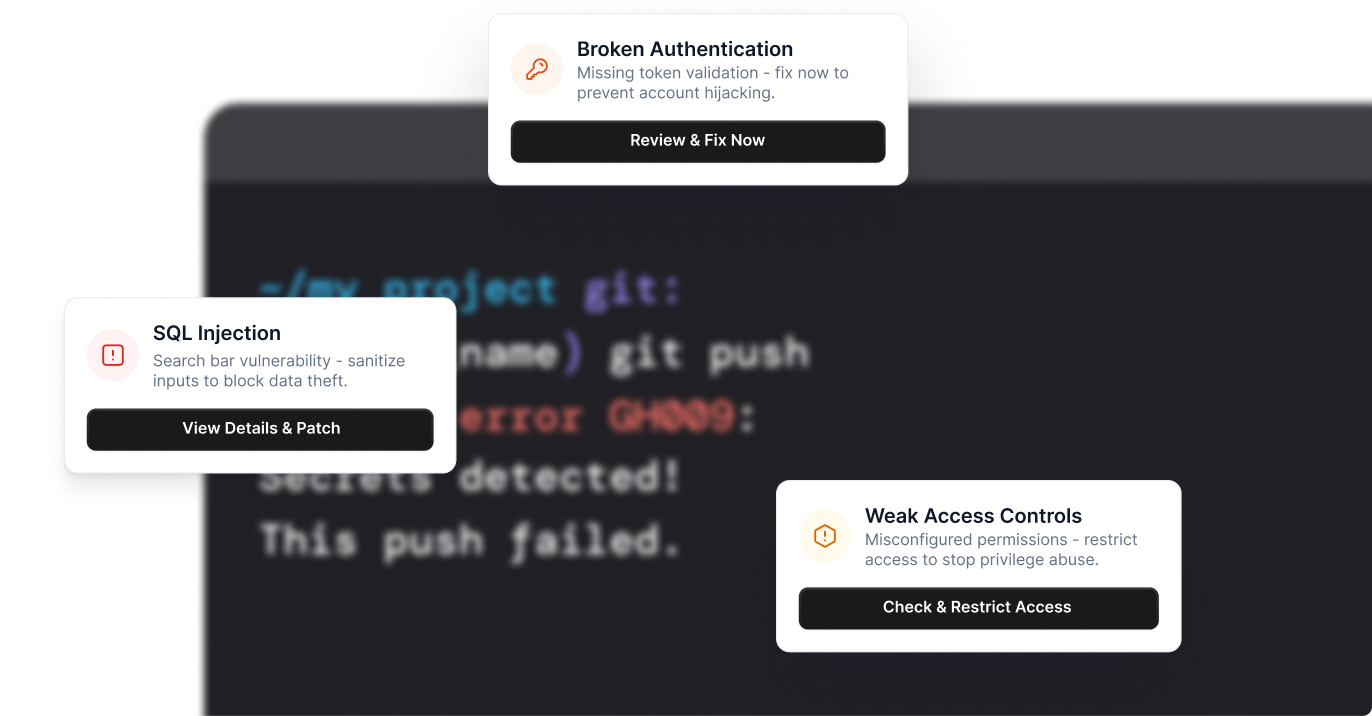
A vulnerability is only a risk if it can be exploited. We identify what truly threatens your security.
02/ Vulnerability Analysis
Detect security flaws using OWASP Top 10 and CWE that could lead to compromise.
- Scan for known vulnerabilities (CVE exploits, misconfigurations, outdated software)
- Identify weak authentication, access control gaps, and risky system settings
- Prioritize critical security gaps based on exploitability and business impact
03/ Exploitation
Validate real-world risks through controlled exploitation. Simulate privilege escalation and provide concrete Proof of Concept (PoC) evidence.

Not all weaknesses are exploitable - we focus on what matters, so you can prioritize effectively.
03/ Exploitation
Validate exploitable vulnerabilities and their impact using NIST and PTES.
- Attempt controlled exploits to assess real security risks
- Simulate privilege escalation, data breaches, and unauthorized system access
- Provide proof-of-concept demonstrations for verified threats
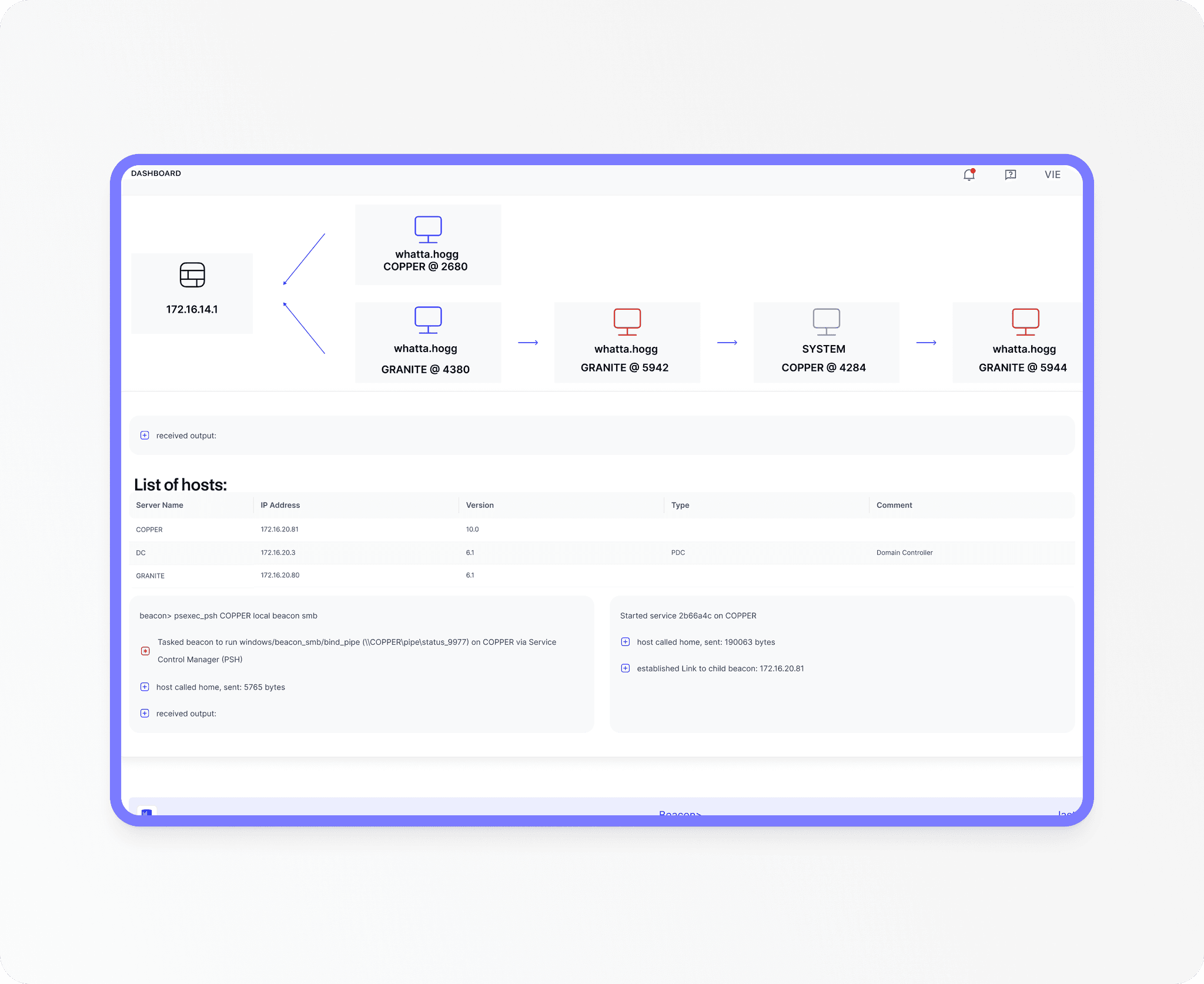
04/ Post-Exploitation
Evaluate the depth of intrusion (lateral movement) an attacker could achieve. Assess the risk of data exfiltration to determine the maximum business impact.

Attackers don’t stop at entry - we test how far they can go and how to stop them.
04/ Post-Exploitation
Assess how deep an attacker could go if a breach occurs.
- Simulate advanced attack scenarios, including lateral movement
- Evaluate potential data exposure, account takeovers, and persistent access risks
- Deliver clear remediation guidance to close security gaps
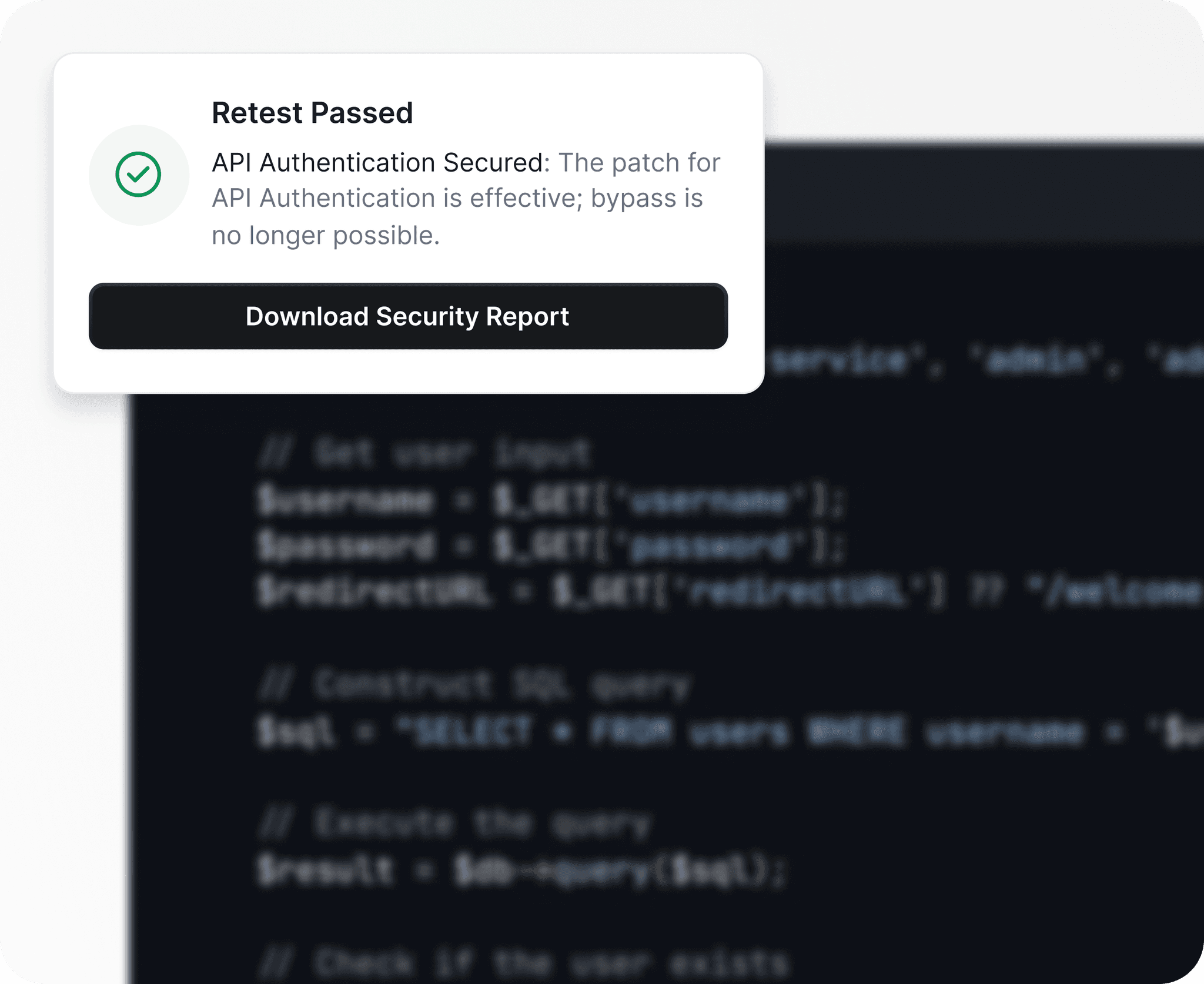
05/ Retesting
Verify that all identified vulnerabilities have been fully remediated by the organization. Detect any new issues that may arise during the patching process.

Fixes can fail or introduce new risks - we ensure your systems stay secure.
05/ Retesting
Ensure all identified vulnerabilities are properly fixed by validating patches against CIS Benchmarks and best practices.
- Verify that previously exploited weaknesses are fully patched.
- Test for new security gaps introduced after fixes.
- Deliver a final security report for compliance and risk management.
Security Standards
compliance
- MITRE ATT&CK® clarify business impact regarding technical risks.
- NIST CSF establish a measurable security roadmap.
- Prioritize critical risks and optimize budget with OWASP
Secure Your Business Today!
Get consultations from a dedicated CyStack’s security experts to deploy your penetration test efficiently and rapidly.
An elite team honored in Global Halls of Fame
Honored for our pivotal role in securing the digital ecosystem through the responsible disclosure of vulnerabilities in industry-leading technologies.







Speakers at prestigious International Forums
Beyond keeping up with the industry, we help shape its future. Our international acclaim is your strongest assurance of receiving world-class Pentest quality.
BlackHat USA
BlackHat Asia

XCon focus
T2FI
FIDO APAC
Taiwan CYBERSEC
Uncover critical vulnerabilities: Case Study from CyStack
Deep-dive into how CyStack researchers secured major platforms.

Affected Target: Cyclos Payment System
Log4Shell vulnerability
A critical Log4j vulnerability in Cyclos enabling arbitrary code execution. Attackers has weaponized it to implant a backdoor within a well-regard cryptocurrency exchange, results in massive data leak.
Click here to download full document
Featured in

Affected Target: D-Link ShareCenter NAS
Remote code execution
The vulnerability affected ~60,000 devices worldwide. Successful exploitation can expose or destroy files on the NAS and turn it into a foothold to attack the internal network.
Click here to download full document
Featured in

Affected Target: Cesanta Mongoose 6.16
Integer overflow
This vulnerability can corrupt memory and potentially allow remote code execution. Because Mongoose is embedded in many devices that rarely receive firmware updates, vulnerable IoT and industrial systems may remain exposed for years.
Click here to download full document

Affected Target: Node.js packages
Prototype pollution
Multiple JavaScript libraries can be manipulated by attackers to modify core objects at runtime. In vulnerable Node.js apps, this can be chained into remote code execution, enabling hijacking of application logic and server takeover.
Click here to download full document
Cut pentesting timelines by 80%
compared to conventional methods
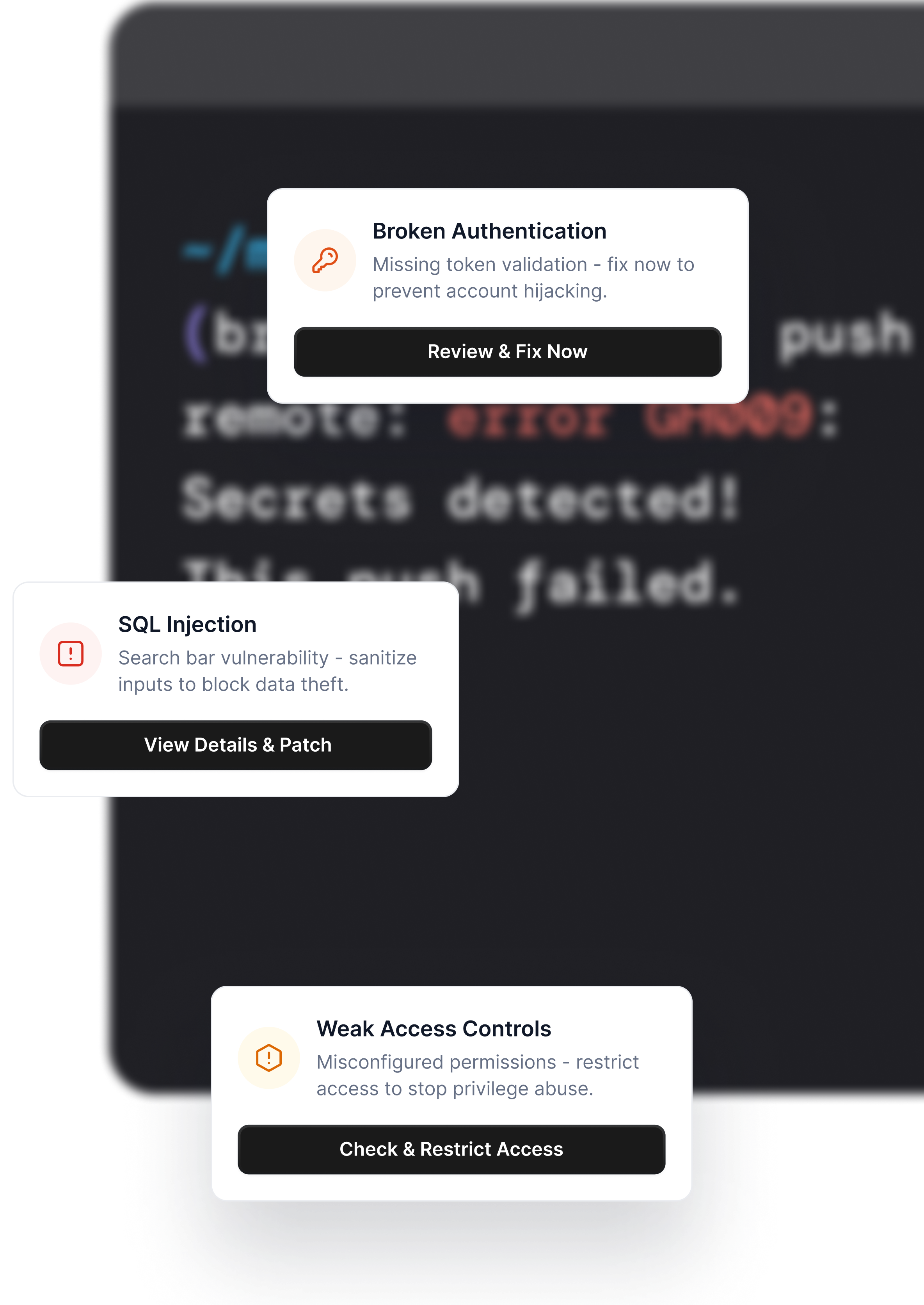
Deliver beyond
what you expected
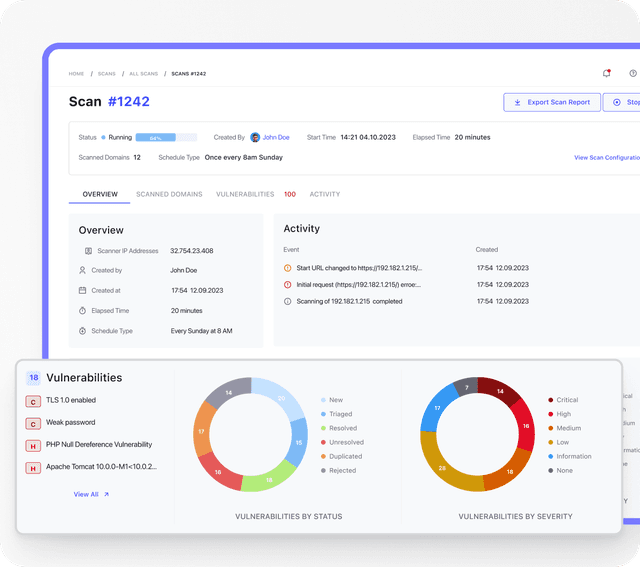
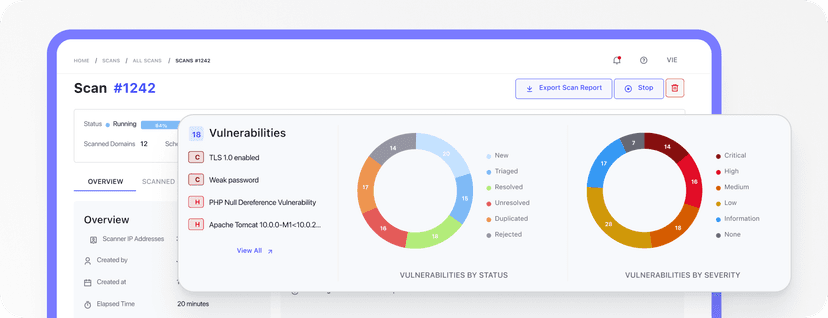
CyStack Platform Access
Track vulnerabilities in real-time, manage fixes in one place, and integrate seamlessly with your existing workflow.
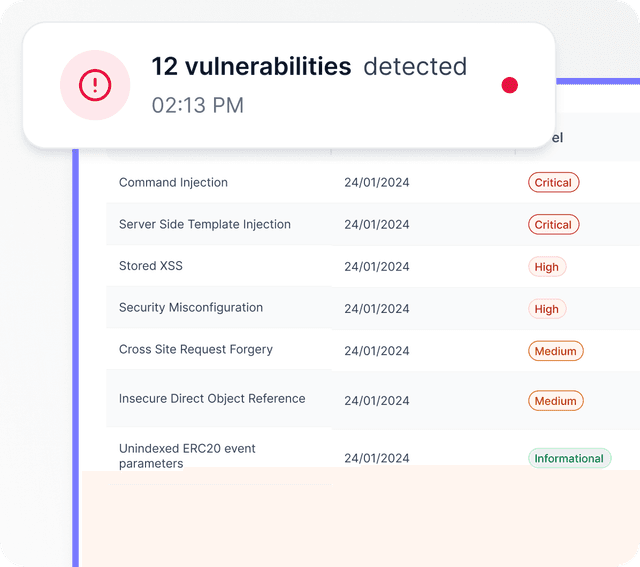
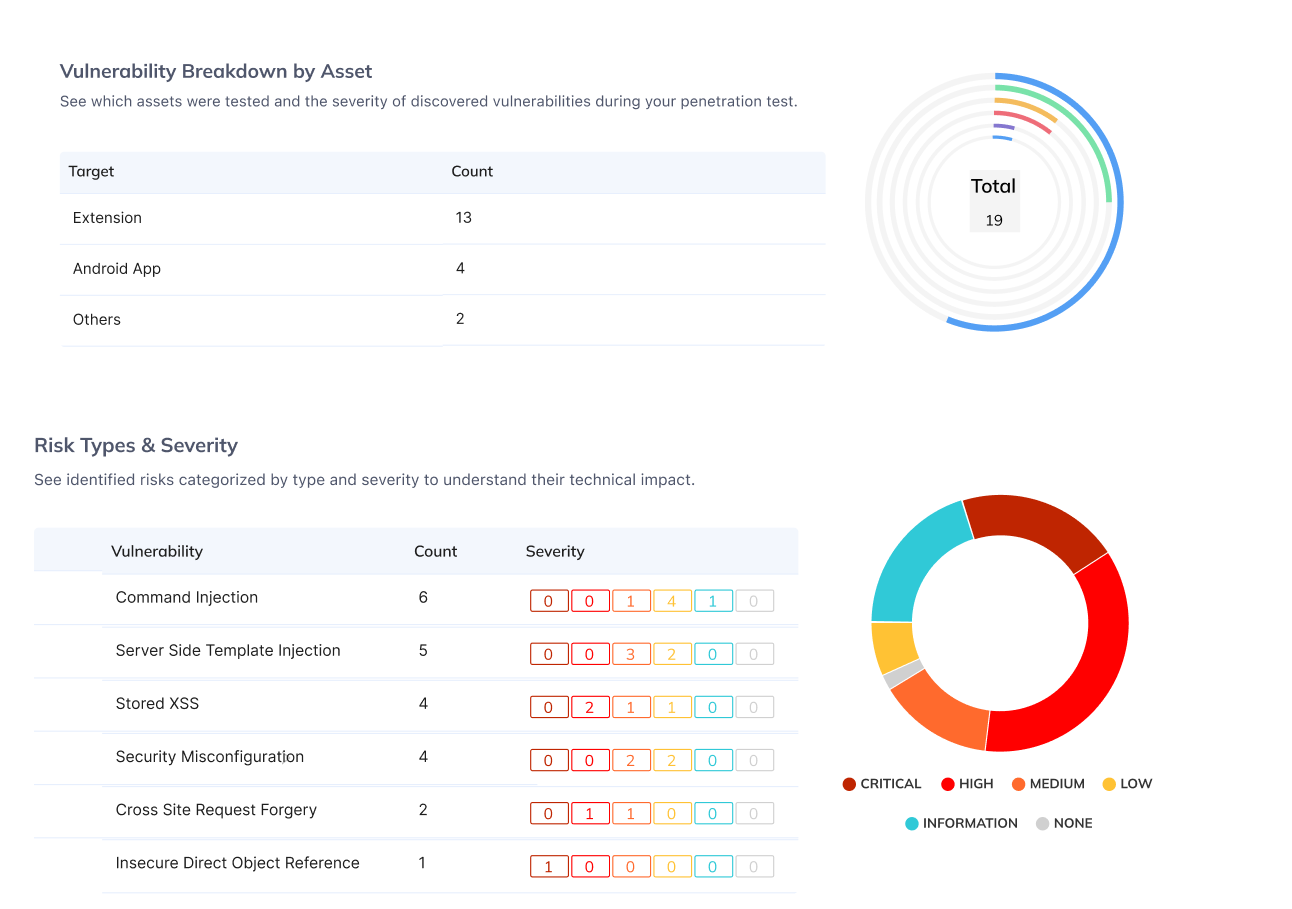
Actionable Report
Detail all identified vulnerabilities, ranked from Critical to Informational, with expert-backed fixes to secure your smart contract.
Validated Certifications
Confirm your systems meet industry security standards and compliance, backed by expert audits and rigorous testing.
Verified Badge
Awarded to systems that pass CyStack’s security standards, proving resilience against vulnerabilities.

Undeniable impact, proven results
Explore our client success stories